What is Hashing: Algorithms and Techniques
|
|
Hashing plays a pivotal role in guaranteeing the integrity and authenticity of data. It is not an encryption technique but is a cryptography method to keep sensitive information and data, including passwords, messages, and documents, confidential and secure.
| Key Takeaways: |
|---|
|
We will learn the following in this article:
|
This article delves into how hashing is used in cryptography, its characteristics, popular algorithms, major use cases, and future trends.
What is Cryptography?
Cryptography is the science of securing communication, ensuring it remains confidential, integral, and accessible only to intended recipients. Many cryptography algorithms are used to encrypt and decrypt data. For more detailed information on cryptography, refer to What is Cryptography?
What is Hashing?
Hashing is a technique that transforms input data of any length into a fixed-size string of characters in a random sequence of numbers and letters.
Hashing Techniques
- The Division Method: Here, you take the key and divide it by the size of the hash table. The remainder of that division is your hash value. For example, if your key is 20 and your hash table has a size of 10, the hash value would be 20 mod 10, which equals 0.
- The Mid-Square Method: Here, you take the key, square it, and then extract the middle digits of the result to use as your hash value. For example, if your key is 56, you would first square it to get 3136. The middle two digits are 13, so that’s your hash value.
- The Folding Method: Here, you divide the key into parts of equal size, then you “fold” them by adding the parts together to create a single hash value. For example, if your key is the phone number 917-555-1234, you would split it into parts like 917, 555, and 1234. Adding them together gives you 2706, which you can then use as your hash value.
- The Multiplication Method: Here, you take the key, multiply it by a special constant number (a floating-point number between 0 and 1), and then take the fractional part of the result. Finally, you multiply that fractional part by the hash table size to get your final hash value.
No matter which technique you use, you’ll sometimes have a collision, which is when two different keys produce the same hash value. Hashing techniques can’t prevent this entirely, so other methods (like chaining or open addressing) are used to handle these collisions and keep the hash table working smoothly. The best hashing technique is one that minimizes these collisions and distributes keys as evenly as possible.
What is a Hash Function?
A hash function performs hashing, and the resultant value is called a hash value, hash code, digest, or hash.
In cryptography, a hash function is a mathematical function that can take any input, such as messages, passwords, or data, and transform it into a fixed-length string.
The importance of hashing lies in its ability to generate a unique “fingerprint” for each input. Any minor change in input will generate a different hash or fingerprint. This quality of hash functions is known as “collision resistance”.
What is a Hash Algorithm?
A hashing algorithm is simply the set of steps or rules that define how the hash function performs this conversion. It is often used interchangeably with a hash function, though there are subtle differences.
Hashing algorithms are generally divided into two main categories based on their purpose: cryptographic and non-cryptographic. The biggest difference between the two is their focus – cryptographic hashes prioritize security, while non-cryptographic hashes prioritize speed.
For example, when we talk about the SHA-256 algorithm, we are referring to the specific mathematical process. When you use a piece of code that implements this process to hash a password, you are using the SHA-256 hash function. Read: Cryptographic Algorithms: Symmetric vs. Asymmetric
Key Characteristics of Cryptographic Hash Functions
In cryptography, hash functions are designed to be:
- Hash functions are deterministic, as the same input will always produce the same hash.
- Computation of a hash is quick, making the hashing algorithms faster.
- Hash functions are irreversible since it is computationally infeasible to reconstruct the original input from the hash.
- The hash function is collision-resistant, as no two input values will generate the same hash.
- Hash functions are hidden since their output makes it difficult to determine their input value.
How Does Hashing Work?
The hashing technique involves three components:
- Input: This is the data entered into the hashing algorithm. The input can be of any length and format, such as a music file or a password string.
- Hash Function: The hash function is the central core part of the hashing technique. This function reads the input string and performs a series of mathematical computations on it to generate a fixed-length string output. Each input piece results in a different output.
- Hash Output: This is also called hash code, value, or simply hash. It is a fixed-length string of characters and numbers. This fixed-length output hash boosts the hash function security, as it is tough to determine the input length based on its output. This output hash is an unreadable string and helps to keep the information private.
The following figure shows the hashing process.

As shown in this figure, an input string of variable length and format is passed to the hash function, which acts on this input and generates a fixed-length output hash. The hash function uses a hashing algorithm to act on the input. The output is the result of the execution of the hashing algorithm.
Hashing vs. Encryption
While both hashing and encryption are cryptography techniques, hashing is fundamentally different from encryption. The following table summarizes the key differences between hashing and encryption:
| Feature | Hashing | Encryption |
|---|---|---|
| Purpose | To ensure data integrity and validate the original data. | To ensure data secrecy and protect sensitive information from unauthorized access. |
| Number of Steps | This is a one-way process that turns data into a fixed-length hash value using a hash function. | A two-way process that converts data into an unreadable form, or ciphertext, using an encryption algorithm and a key. |
| Key Required | No key is required. | It requires encryption and decryption keys to convert data between plaintext and ciphertext. |
| Speed | Hash functions are fast and efficient, generating unique hash values for each input. | Encryption algorithms are slower than hashing, especially asymmetric encryption. |
| Output Size | Has fixed Length. | It is a variable (can be equal to input). |
| Reversibility | It is irreversible as the output cannot be reversed to get the original data. | Reversible with a key, and the process is called decryption. |
| Use Case | Common applications include storing passwords, creating digital signatures, and verifying data integrity. | Encryption is used for secure communication, data storage, and securing sensitive information. |
| Common Algorithms | MD5, SHA-3 and SHA-256. | Rivest-Shamir-Adleman (RSA), Advanced Encryption Standard (AES), and Blowfish. |
Read: What is Encryption? Process, Benefits, and Applications
Properties of a Cryptographic Hash Function
A cryptographic hash function has the following properties:
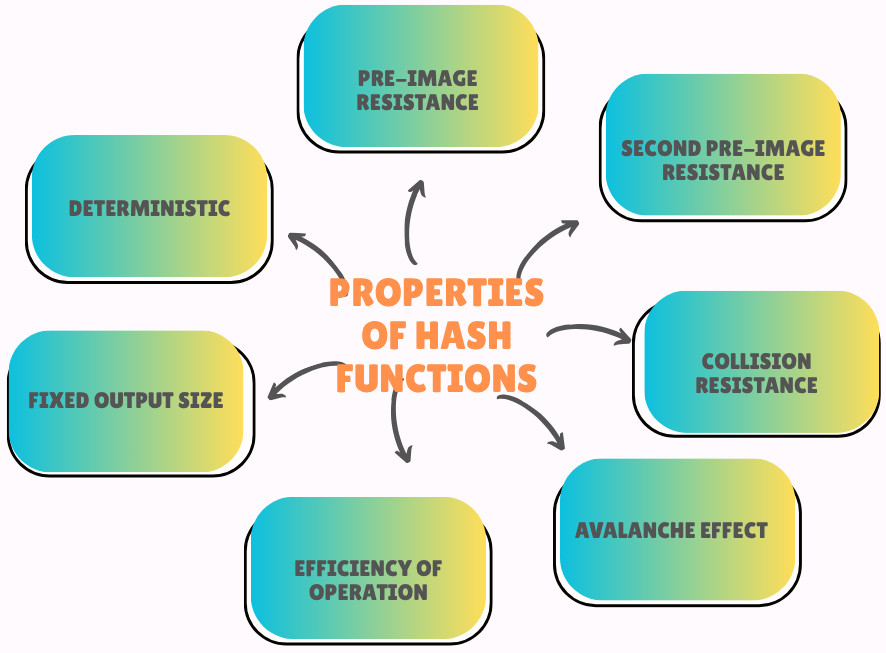
Pre-image Resistance
According to the pre-image resistance property, reversing a hash function should be computationally demanding. For example, if a hash function h generates a hash value H, retrieving the input value x should be difficult such that hash(x) = H.
This feature defends against attacks to locate the input with just the hash value.
Second Pre-image Resistance
According to the second pre-image resistance property, finding another input with the same hash should be difficult. Given an input x1, it should be hard to find another x2 such that x1 ≠ x2 and hash(x1) = hash (x2).
This property also protects against an attack that intends to replace the original input and hash with a new value.
Collision Resistance
A hash function is a compression algorithm with a fixed-length hash and is not free of collisions. The collision-free property indicates that these collisions are hard to locate.
Finding any two distinct inputs x1 and x2 should be challenging, such as hash(x1) = hash(x2).
This property ensures data integrity and uniqueness.
Avalanche Effect
According to this property, a slight change in input should result in a hash that looks completely different. This protects against minor tampering.
For instance, if x1 = “Hello” produces H, then a slight change in x1, like x1 = “hello”, will create a different hash not equal to H.
Efficiency of Operation
Hash functions are computationally faster than symmetric encryption. Computing h(x) for any hash function h given input x is easy.
Fixed Output Size
A hash function generates a fixed-length output regardless of the input size and format. It helps produce outputs of the same size from different input sizes.
Deterministic
The hash function consistently produces the same output for a given input, like a recipe that yields the same dish when followed precisely.
Types of Cryptographic Hashing Algorithms
A hash function is a mathematical function that takes two data blocks of fixed size and converts them into a hash code. It is a key part of the hashing algorithm. The length of these data blocks depends on the algorithm used, but they usually range from 128 bits to 512 bits.
Before we figure out the different hash functions, keep in mind the following points related to hash functions and algorithms:
- Hashing algorithms process messages using a sequence of rounds, similar to a block cipher.
- Each round uses a fixed-size input, which usually combines the current message block and the result from the previous round.
- This process continues for multiple rounds until the entire message is hashed.
- The hashing operations are interconnected; one operation’s output affects the next one’s input. Therefore, a minor change in the original message can drastically alter the final hash value. This is the Avalanche effect.
- There is a distinction between a hash function and a hashing algorithm. The hash function itself takes two fixed-length binary blocks of data and generates a hash code. A hashing algorithm, on the other hand, establishes how the message is divided into blocks and how the outcomes of multiple hash operations are combined.
- Hash functions play an important role in computing, providing versatile capabilities such as quick data retrieval, secure information protection (cryptography), and ensuring data remains unaltered (integrity verification).
Some of the most popular cryptographic hash algorithms are:
Message Digest Algorithm 5 (MD5)
MD5 is the most popular and often used hash function. MD2, MD4, MD5, and MD6 are members of the MD family, which was adopted as the RFC 1321 Internet Standard.
It is a 128-bit hash function that ensures the integrity of transferred files. File servers frequently provide the MD5 feature to enable users to compare the checksum of the downloaded file with the pre-computed MD5 checksum.
MD5 is known for its speed, but in 2004, collisions were found in MD5. It was claimed that an analytical attack using a computer cluster could breach it in under an hour. Since it was compromised, MD5 was deprecated in most security-sensitive contexts.
Secure Hash Algorithm 1 (SHA-1)
The first iteration of the 160-bit hash algorithm, SHA-0, was released by the National Institute of Standards and Technology (NIST) in 1993. However, it had a few drawbacks and didn’t gain much attention.
SHA-1 was created in 1995 and is the most widely used of the existing SHA hash functions. It generates a 160-bit hash and is used in most applications and protocols, including Secure Socket Layer (SSL) security.
SHA-2 (Secure Hash Algorithm 2)
SHA-2 is still considered secure and is widely used. SHA-224, SHA-256, SHA-384, and SHA-512 are the four variants of SHA-2 family. These versions vary depending on the number of bits in their hash value. This hash function has not been the target of any attacks so far.
Though SHA-2 is a strong hash function, its basic design still follows that of SHA-1. SHA-2 is widely used in SSL certificates, digital signatures, and Bitcoin.
SHA-3
This is a newer standard and is an alternative to SHA-2. It is based on the Keccak algorithm that is known for its effective operation and strong attack resistance. This algorithm is mainly designed for flexibility and enhanced security.
BLAKE2 and BLAKE3
BLAKE2 is a fast and secure hash function that improves SHA-3. There are two versions of this algorithm, BLAKE2b and BLAKE2s.
BLAKE2b is suitable for 64-bit computers and produces hash values up to 512 bits long.
BLAKE2s is used for smaller computers (up to 32 bits) and produces a hash value of up to 256 bits.
The algorithms are high-speed and secure. They are considered modern alternatives to SHA algorithms and are growing in adoption.
Standard Length of Hash Functions
Hashing converts a data set of any size into a shorter, fixed-length output using a mathematical formula. This section demonstrates the output obtained for a specific input string using different hash functions.
Hashing Algorithm Examples
The following table provides the hash values obtained from MD5, SHA-1, and SHA-256 hash functions on the string “Cryptography”.
| Input Message | Hash Function | Hash Value |
|---|---|---|
| Cryptography | MD5 (128-bit, 16-byte) 32 characters | 64ef07ce3e4b420c334227eecb3b3f4c |
| Cryptography | SHA-1 (160-bit, 20-byte) 40 characters | b804ec5a0d83d19d8db908572f51196505d09f98 |
| Cryptography | SHA-256 (256-bit, 32-byte) 64 characters | b584eec728548aced5a66c0267dd520a00871b5e7b735b2d8202f86719f61857 |
As seen in the above table, each algorithm produces a unique hash with a fixed length. MD5 generates a hash with 32 characters, while SHA-1 and SHA-256 generates hash values of length 40 and 64, respectively.
Note: The above outputs of hash functions are generated using the Python library, hashlib.
Applications of Hashing in Cryptography
Here are a few examples of applications of hashing in Cryptography:
Password Storage
Hash functions protect the password storage. Instead of storing passwords in plaintext, systems hash them and store the hash in a file. A typical password file is a table of pairs in the format (user id, h(P)) where h(P) is the hash value of the password.
Hence, even if attackers have access to the password, all they can see is the hashes of the password. Read: Authentication vs. Authorization: Key Differences
Digital Signatures
Hash functions are integral to digital signatures, which verify the authenticity and integrity of a message or document. Hashing is used in digital signatures to verify the sender’s identity and ensure the document hasn’t been tampered with. Only the hash of the data is signed, not the data itself.
Data Integrity Verification
Data integrity is verified using hashing to ensure the data has not been altered. For example, file downloads often come with a hash to confirm the file wasn’t corrupted or tampered with.
However, an attacker could modify the entire file and generate a new hash, sending it to the receiver. Thus, it does not guarantee the authenticity of the file and is only effective if the user trusts the file’s source.
Blockchain and Cryptocurrencies
Blockchain technology is one of the most publicized applications of hashing and is used specifically with cryptocurrencies like Bitcoin. In a Blockchain, blocks are linked using cryptographic hashes. If someone tries to alter the transaction history in the block, the hash values would change, and the transaction would be invalid. Hashing ensures data authenticity and integrity in Blockchain when everyone has access to the same data. Read: Blockchain Testing: How to do it?
Disadvantages of Hash Functions
Hashing does have some disadvantages, some of which are listed here:
- Risk of Collisions: Hash functions can sometimes suffer from collisions when two different outputs produce the same hash value. This can lead to reduced performance and increased lookup time if collisions are high.
- Non-reversible: Hash functions are one-way, and reversing the process to get the original input data is computationally infeasible. This becomes a drawback when a reverse lookup is necessary.
- Limited Sorting: When data needs to be sorted, hashing is not an ideal option. This is because the internal representation of hashes, called hash tables, doesn’t provide inherent support for sorting.
- Space Overhead: Hashing requires more storage space to store hash values and related data, which can be substantial when big data sets are involved.
- Key Dependency: Hash functions rely on the uniqueness of keys to ensure efficient data retrieval. If the keys are not unique, collisions can occur, leading to performance bottlenecks.
Best Practices for Secure Hashing
For secure hashing, the following best practices should be followed:
- Avoid Insecure Algorithms: Never use deprecated hash functions like MD5 or SHA-1 for security-sensitive tasks.
- Use Salting: Always salt (add a unique, random string of characters or the “salt” to each password before hashing it) passwords before hashing.
- Use Key Stretching: Employ modern algorithms like bcrypt, scrypt, or Argon2 for password hashing.
- Update Hash Functions Periodically: Stay up-to-date with hash functions as older hash functions become vulnerable with an increase in computational power.
- Combine with Other Security Measures: Do not rely on hashing alone for authentication or encryption.
Future of Hashing in Cryptography
Traditional hash functions may become vulnerable as computing capabilities grow and quantum computing approaches practical viability. Research is in progress into:
- Quantum-resistant algorithms.
- Post-quantum cryptographic hashing standards.
- More efficient and secure hash functions like BLAKE3.
Conclusion
Hashing in cryptography is an important technique that ensures data integrity, authentication, digital signatures, and the security of modern digital infrastructure. Understanding the entire process, hash functions, principles, limitations, and correct applications is crucial for cybersecurity, software engineering, and IT professionals.
It is essential to choose the correct algorithm for the task and protect against known attacks through techniques like salting and key stretching and by adhering to standard practices.
In the digital era, which is increasingly dependent on secure data transmission and trustless systems like Blockchain, hashing is more critical than ever.
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












