Browser Sandboxing Explained
|
|
The IT industry is rapidly evolving thanks to the enhancements in technology. However, every basket has a few rotten apples; for this industry, it is cybercrime.
“Cybercrime is predicted to cost the world $10.5 trillion annually by 2025.” (source)
Cybersecurity has gained momentum to safeguard software from these threats. It has become an essential aspect of the IT industry and virtually every other sector, like banking, government, education, defense, retail, healthcare, and more.
Among the various cybersecurity strategies like multi-factor authentication, firewalls, encryption, and VPNs, one other technique is sandboxing.
Read on to learn more about sandboxing and its different types, and delve into browser sandboxing.
What is sandboxing?
As a kid, you might have had your own colorful pale and spade to carry to the beach. With the help of these tools, you might have built sand castles or other sculptures, demolished them, and started all over again.
When you were building your mighty sand castle on the beach, and if you were too close to the sea, a tide could wash your efforts. Or, let’s say you just finished building a beautiful sand castle, and a frisbee lands right on top of it, misshaping the whole castle. Well, that’s disappointing.
The online world is like a beach, filled with many disruptors in the form of waves, wind, and frisbees. Using the tools, you can build your application. Still, there could be potentially damaging, even malicious content out there, like that frisbee that landed on your castle, that could corrupt your application and your system.
But what if you built the same castle in a protected environment like a sandbox, like the ones you see in playgrounds? They are enclosed, protected territories, suitable for the user to operate in without worrying about waves washing out their hard work.
Types of sandboxing
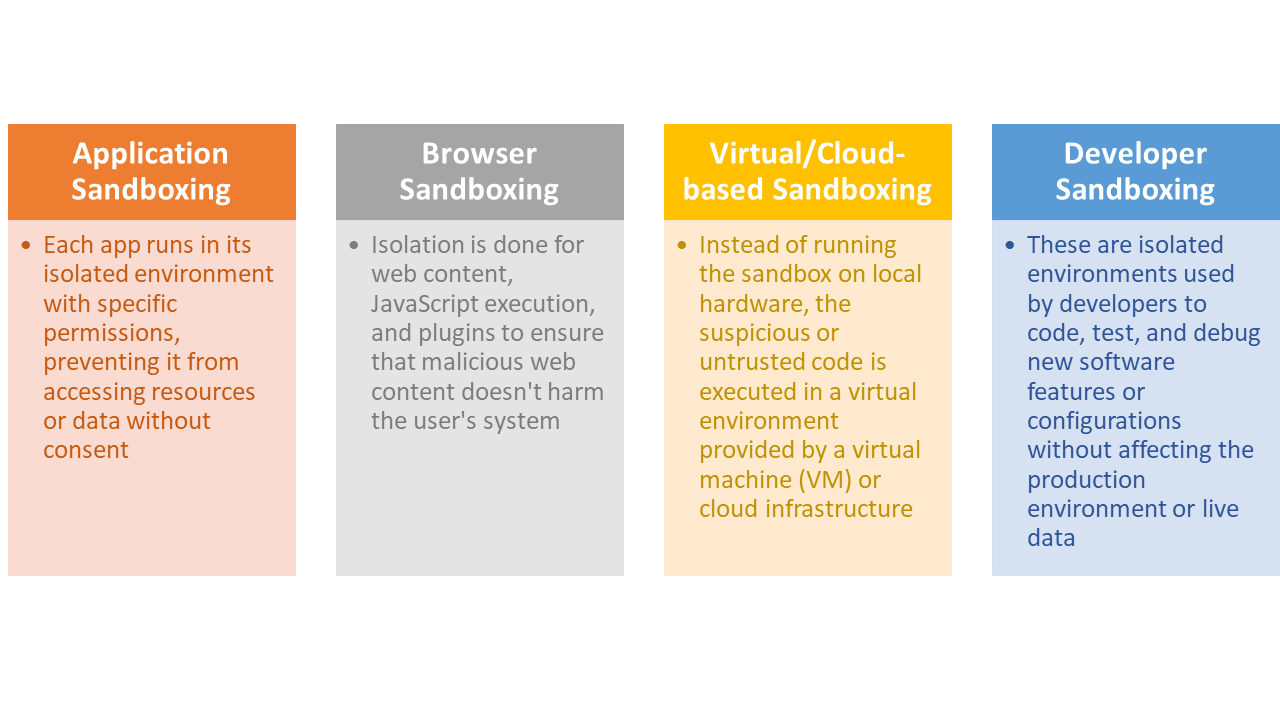
More about browser sandboxing
In lieu of the above discussion, browser sandboxing is a security mechanism meant to isolate web content in a confined environment, preventing it from causing harm or accessing sensitive system resources. The primary objective is to protect the user and their system from potential malicious actions initiated by content on the web, such as harmful scripts.
Some commonly used terms in browser sandboxing
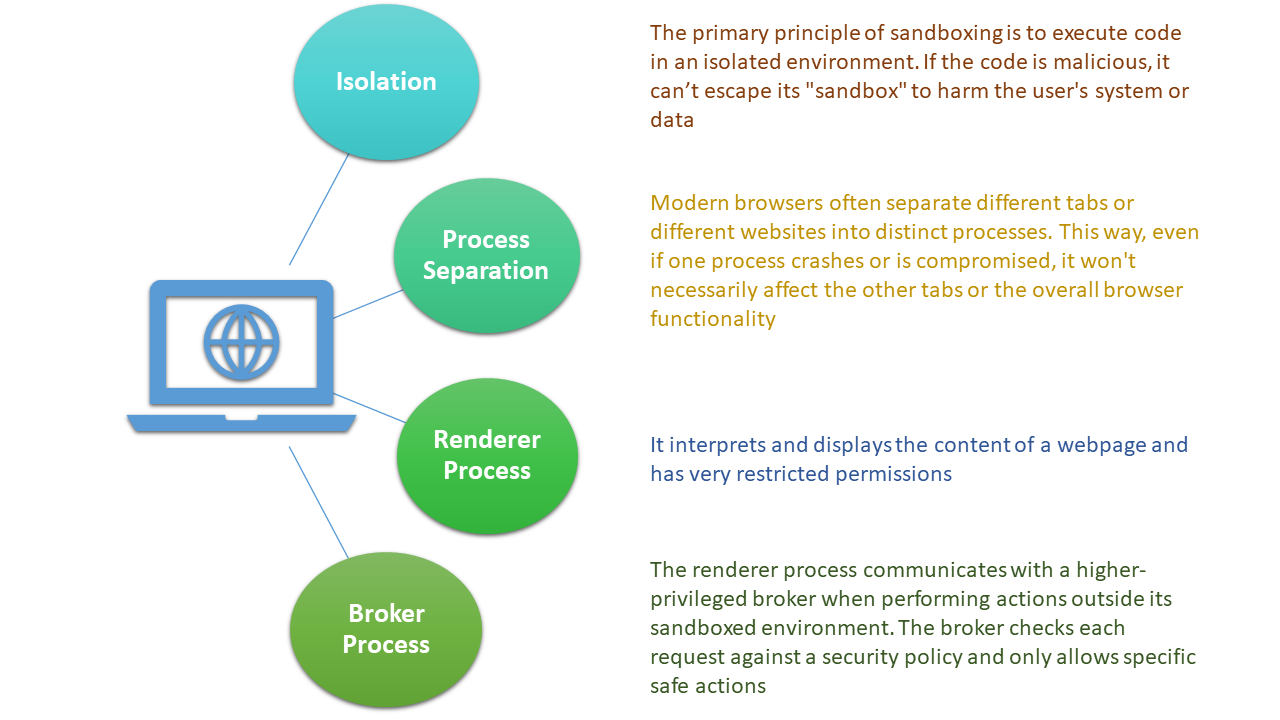
Ways to do browser sandboxing
When it comes to browser sandboxing, we saw that the main aim is to isolate your machine from cyber attacks that can happen when you go online. Local browser isolation and remote browser isolation are two approaches to sandboxing that focus on where and how web content is processed and rendered.
Local browser isolation
The virtual browser is run in a controlled, isolated environment, like a virtual machine, using the user’s local device. Consider a user visiting a website with an embedded malicious script in a browser like Chrome. The malicious script is executed within a restricted renderer process specific to that tab. Even if the script exploits a vulnerability in the rendering engine, it remains confined to that sandboxed process and cannot freely access system resources or data. The malicious actions would be restricted within the boundaries set by the browser’s sandboxing mechanisms.
Remote browser isolation
In this technique, web content is not directly processed or rendered on the user’s device but rather on a cloud-based or organization server. Imagine a user who wants to visit a website, but instead of the browser on their computer directly fetching and rendering the site, a remote server does this task. The server processes the site, runs any scripts, and then sends a visual representation of the site to the user’s computer. So, even if the website contains malicious scripts, they execute in the isolated environment on the server, not the user’s device. The user’s device only displays the “safe” visual representation, ensuring a layer of protection against web-based threats.
There are two methods in remote browser isolation for achieving the separation between the user’s local infrastructure and web content.
Pixel Streaming
Over here, the remote server processes and renders the web content in an isolated environment. Instead of sending the actual content to the user’s device, the server captures a visual representation, like a video feed of the website. It streams this display data to the user’s device. Since only pixels are streamed to the user’s device and not the actual content, potential threats like malicious scripts, downloads, or compromised ads remain confined to the remote environment and never reach the endpoint.
DOM (Document Object Model) Mirroring
Instead of streaming pixels, DOM mirroring involves sending a safe version of the website’s DOM structure to the user’s local browser. The actual web content, including any scripts, is executed and processed on the remote server.
Browser sandboxing in different browsers
Luckily, most popular browsers have sandbox mechanisms built into them. For example, Google Chrome is sandboxed by default for its users, Mozilla Firefox provides selective sandboxing implementations, while Apple’s Safari runs websites on separate processes.
Firefox browser sandbox
The Firefox browser executes untrusted code in a sandbox environment to prevent it from affecting the user’s system. Such code is run using parent-child processes where the parent process mediates between the user’s resources, and the child processes run in the sandbox. There are different levels of restrictions, with level 0 being the lowest level. Firefox’s sandbox thus controls the limit of exposure the untrusted code gets to the user’s resources, preventing it from infecting the user’s system.
You can check the level of sandboxing using the about:config command.
Chromium browser sandbox
Both Google Chrome and Microsoft Edge browsers use Chromium sandbox, similar to how Firefox sandbox runs. Here, the parent processes are the broker processes, and the child processes are called target processes. This means that all code run by target processes is run in the sandbox.
Edge browser sandbox
When you run the Edge browser in the sandbox environment on Windows 10, you will see a fresh desktop where the start menu and other icons are visible but not functional. Closing the sandbox browser means losing all traces of activities done in that sandbox environment.
Though your ISP might keep a log of activities, even if any malware is installed into your system, it will get discarded once you close the sandbox window.
Google Chrome browser sandbox: how to turn it off?
By default, the sandbox is enabled, but to turn it off, you need to right-click on its icon, click on Properties, and then on the Shortcut tab in the dialog box.
Add the following to the app path shown in the Target: --no-sandbox
After this, whenever you click the Chrome icon, it will load Chrome without a sandbox.
Final note
While browser sandboxing provides a substantial layer of security, it’s not infallible. Security researchers and hackers continually discover new methods to bypass these mechanisms, which is why browsers regularly update to patch known vulnerabilities and improve their sandboxing techniques. Users need to keep their browsers updated to benefit from these security enhancements continuously.
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












