Cryptographic Algorithms: Symmetric vs. Asymmetric
|
|
In this era of digital communication, data protection is of paramount importance. Cryptography, derived from the Greek words kryptos (meaning hidden) and graphein (meaning to write), is a science of protecting data and is the cornerstone of secure digital communication.
| Key Takeaways: |
|---|
|
This article thoroughly explores symmetric and asymmetric cryptography, including its theoretical foundations, algorithmic design, advantages, weaknesses, and uses in real-world settings.
What are Cryptographic Algorithms?
Cryptography is the science of encoding and decoding information to secure it from unauthorized access. It hides the information transmitted by the sender so that it is read only by the intended receiver.
Cryptography involves transforming plaintext (in readable form) into a ciphertext (unreadable or encrypted data) using data encryption algorithms. At the receiver’s end, the process is reversed. The incoming ciphertext is transformed into plain text using decryption.
For more information on Cryptography, refer to What is Cryptography? The entire process of cryptography is summarised in the following diagram:
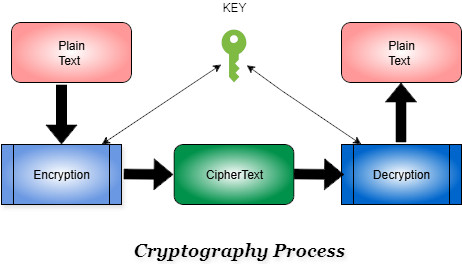
The two blocks represented above, marked encryption and decryption, are steps used to convert plain text to ciphertext and back, respectively. These steps are known as Cryptographic Algorithms, also known as Encryption algorithms.
A cryptographic algorithm hides or encrypts data using an encryption key. Encryption means converting readable data into an unreadable format or ciphertext. This ciphertext is converted back to readable data using the decryption key. Secrecy and strength of the encryption keys and algorithms determine the effectiveness of cryptography. The cryptographic algorithms are broadly divided into:
- Symmetric Key Cryptography
- Asymmetric Key Cryptography
This division is based on the encryption key used in the cryptography process at the sender’s and receiver’s ends. Each approach has its advantages, disadvantages, and specific applications, which are discussed in detail in the remainder of this article.
Symmetric Cryptography
Symmetric cryptography, also known as secret-key cryptography, uses a single key for encryption and decryption, called a secret key. The sender and the receiver must both possess this key and keep it secret.
How Symmetric Cryptography Works
The process of symmetric cryptography/encryption is shown below:
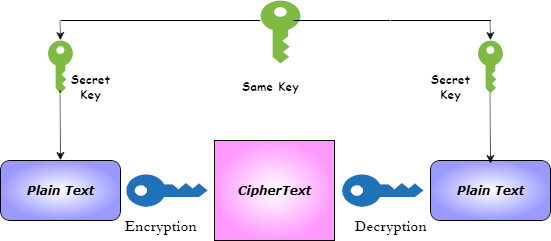
- Encryption: Plaintext (readable data) is encrypted using a shared secret key into a ciphertext (unreadable form).
- Transmission: The encrypted message (ciphertext) is sent to the recipient.
- Decryption: The recipient decrypts the ciphertext into plain text using the same key.
Commonly Used Symmetric Algorithms
Here are some of the commonly used symmetric algorithms:
Data Encryption Standard (DES)
DES is an older encryption algorithm that converts 64-bit plaintext data into a 56-bit key to perform 16 rounds of encryption. This algorithm, introduced in the 1970s, uses a symmetric key to encrypt/decrypt the information. It is considered a building block for other encryption algorithms. It used both transposition and substitution cipher techniques for encryption.
DES was designed for hardware and not software. It shows efficiency and fast implementation in hardware. However, it is now considered insecure mainly because of its short key length.
Triple DES (3DES)
3DES is an enhancement of DES that overcomes its shortcomings. 3DES or Triple DES is a symmetric algorithm that uses three different keys (K1, K2, and K3) and applies DES in a specific sequence: encrypt with K1, decrypt with K2, and encrypt again with K3. Thus, it triples the 56-bit key into a 168-bit one. Due to the same process being applied thrice, 3DES is slower than its more modern counterparts. Furthermore, using small data blocks increases the risk of decryption by brute force.
Advanced Encryption Standard (AES)
AES is the most widely used symmetric algorithm today. It was developed in 2005 as a replacement for the outdated DES. AES encrypts fixed-size blocks of data (128 bits) and supports key sizes of 128, 192, and 256 bits. The algorithm is efficient for both software and hardware implementations. The algorithm encrypts one block at a time in what are called “rounds.” The data is first converted into blocks and then encrypted with the key in different rounds based on the key size.
There are many types of AES depending on the rounds:
- AES-128 uses 10 rounds
- AES-192 uses 12 rounds
- AES-256 uses 14 rounds
The encryption process involves a series of data manipulation and mixing steps in each round, such as substitution, transposition, mixing, column mix, and sub-bytes. AES has not been cracked and is considered very secure, especially with more extended key sizes like 256 bits. It is widely used in Government and Military, Wireless Networks, Website security, and processor security, to name a few.
Blowfish and Twofish
These are the fast block ciphers developed to replace DES. Both offer variable-length keys and are popular for their speed and effectiveness. Blowfish is a symmetric algorithm and a block cipher like AES, with a key length varying from 32 bits to 448 bits. It was designed as a public tool that is not licensed.
Twofish is its upgraded version, which utilizes a block size of 128 bits that is extendable up to 256 bits. The main feature of these two algorithms is that they utilize 16 rounds of encryption, independently of the key or data size.
Advantages of Symmetric Cryptography
Symmetric cryptography has the following advantages:
- Uses the same key for encryption and decryption.
- They are faster and more efficient for larger amounts of data.
- Symmetric algorithms are simple and conceptually more straightforward to implement.
- It uses a secure method to share the key between sender and receiver, which protects the key and makes the approach safer.
Disadvantages of Symmetric Cryptography
Some of the disadvantages of symmetric cryptography are:
- Key distribution or securely sharing the secret key with all parties can be challenging.
- In an extensive network, the number of keys required grows exponentially. For example, in a network of ‘n’ users, the number of keys = n(n-1)/2.
Real-World Applications
Symmetric cryptography has the following real-world applications:
- Disk Encryption, like BitLocker: BitLocker is activated on a Windows computer to encrypt all hard drives. By unlocking the PC with a password, the user decrypts the data without the risk of exposing the secret encryption key.
- File Encryption Software (AxCrypt): File encryption software mainly employs the AES symmetric algorithm to protect sensitive data stored on devices. This ensures data remains secure even if the device is stolen or lost.
- Secure Messaging Apps (WhatsApp): Messaging applications like WhatsApp use symmetric encryption to ensure that messages are encrypted end-to-end, allowing only the intended recipients to read them.
- Virtual Private Networks (VPNs): They use symmetric key encryption to establish secure communication channels, enabling remote users to connect to corporate networks securely.
Asymmetric Cryptography
Asymmetric cryptography, or public-key cryptography, uses a pair of keys: a public key and a private key or a decryption key. What one key encrypts, only the other can decrypt. However, neither key performs both functions. It was created to solve the problem of symmetric encryption, which involves sharing a single encryption key used for encryption and decryption.
How Asymmetric Cryptography Works
The process of asymmetric cryptography is shown below:
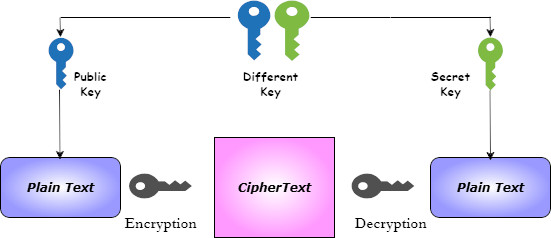
-
Encryption: The sender encrypts data into a ciphertext using the public key for encryption and the private key for decryption.Note: The public key is available to anyone who wants to encrypt. But this key doesn’t work for decryption. A user needs to have a separate private key for decryption. This secondary private key is only held by the one who decrypts the data.
-
Decryption: The recipient decrypts the message using their secondary private key.
- Digital Signatures: The sender can use digital signatures to sign a message using their private key. This way, the sender can be verified.
Commonly Used Asymmetric Algorithms
Asymmetric cryptography has some popular algorithms discussed here:
Rivest-Shamir-Adleman (RSA)
RSA is one of the first public-key cryptosystems and is considered the staple of asymmetric cryptography. One of the first public-key cryptosystems, RSA, was developed by engineers (Rivest, Shamir, and Adleman) in 1977 and is widely used for secure data transmission and digital signatures. It uses factorization of the product of two prime numbers to deliver encryption of 1024 bits and up to 2048-bit key length.
The following steps achieve RSA key generation:
- Two large prime numbers, p and q, are chosen and kept secret.
- The value of ‘n’ is calculated as n=p*q.
- Next, Euler’s totient function, given by φ(n) = (p-1) * (q-1), is calculated.
- An integer e is chosen such that 1 < e < φ(n) and gcd(e, φ(n)) = 1.
- An integer d is calculated as (d*e) % φ(n) = 1.
- The public key is (n,e), where e is the public exponent.
- The private key is (n,d), where d is the private exponent.
Once the public and private keys are obtained, the sender encrypts the data using the receiver’s public key (n,e) and the “mod” function to calculate the ciphertext. The receiver decrypts the ciphertext using the private key (n,d). The level of security provided by RSA is incomparable, and according to research conducted in 2010, cracking RSA’s smaller 768-bit version will require 1500 years of computational power!
However, this means that RSA is a slower algorithm. The process is slower but highly secure since it requires two different keys for encryption and decryption.
Elliptic Curve Cryptography (ECC)
ECC is a public key cryptography (asymmetric) method that relies on the algebraic structure of elliptic curves (a specific equation over a finite field) on finite fields (a set of numbers with particular arithmetic rules). The key is generated by selecting an elliptic curve and a point on the curve. The user then chooses a private key (a random integer). The public key is obtained by multiplying the selected point by the private key. The sender uses the recipient’s private key to encrypt the data, and the recipient uses their private key to decrypt the ciphertext.
ECC offers security similar to traditional methods like RSA but with significantly smaller key sizes, making it suitable for resource-constrained environments.
Digital Signature Algorithm (DSA)
DSA is primarily used for digital authentication rather than encryption. This algorithm generates and verifies digital signatures. DSA is a public-key cryptosystem that uses mathematical concepts of modular exponentiation and the discrete logarithm problem. The generated digital signatures then verify the authenticity and integrity of digital documents.
Using DSA, the user generates a private key (secret) and a corresponding public key (shared). The message or document is signed using a private key and a secure hashing algorithm (like SHA-256) to create a digital signature. The sender’s public key is used when the recipient wants to verify the digital signature.
Advantages of Asymmetric Cryptography
Some of the advantages of asymmetric cryptography are as follows:
- Uses two keys, a public key for encryption and a private key for decryption, making the process secure.
- This approach solves the key distribution problem as sharing private keys is unnecessary.
- Asymmetric cryptography enables digital signatures, ensuring data authenticity and non-repudiation.
- Public keys can be shared without compromising security.
Disadvantages of Asymmetric Cryptography
Asymmetric cryptography has the following drawbacks:
- Asymmetric cryptographic algorithms are much slower than symmetric encryption, especially for large data volumes.
- These methods require more processing power and memory, as generating public and private keys involves many calculations.
Real-World Applications
- Secure Email Communications: Secure email communication protocols like Secure Multipurpose Internet Mail Extensions (S/MIME) use asymmetric cryptography. They use public and private keys to encrypt email content, ensuring only the correct recipient with a valid private key can decrypt the message.
- HTTPS (SSL/TLS): The Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols use asymmetric cryptography to secure data transmission between a user’s browser and a website. Asymmetric encryption is used for the initial handshake process to secure the exchange of a symmetric encryption key. This key is then used to encrypt and decrypt data for the session.
- Digital Signatures: Digital signature services like Adobe Sign and DocuSign use asymmetric cryptography. A user signs a document digitally, creating a unique signature with their private key. The recipient then verifies the authenticity and integrity of the document using the sender’s public key.
Symmetric vs. Asymmetric Cryptography
The following table summarizes the key differences between symmetric and asymmetric cryptography:
| Feature | Symmetric Cryptography | Asymmetric Cryptography |
|---|---|---|
| Size of ciphertext | The same or smaller than the original plain text | The same or larger than the original plain text |
| Data size | Used for large amounts of data | Used for small amounts of data |
| Resource Utilization | Low | High |
| Key Lengths | 128 or 256 bits | 2048 bits or higher |
| Security | Less secure, as only one key is used for both encryption and decryption | More secure as two keys are used, one for encryption and the other for decryption |
| Number of keys | One secret key for both encryption and decryption | Two keys, a public key and a private key, one for encryption and the other for decryption |
| Techniques | It is an old technique | It is a modern encryption technique |
| Confidentiality | A single key for encryption and decryption has a chance of key compromise | Two keys, separately made for encryption and decryption, that remove the need to share a key |
| Speed | Symmetric encryption is a fast technique | Asymmetric encryption is slower in terms of speed |
| Algorithms | AES, DES, 3DES, and QUAD | RSA, ECC, and Diffie-Hellman algorithms |
Hybrid Cryptographic Systems
To use the strengths of both symmetric and asymmetric approaches, modern cryptographic systems employ a hybrid approach that combines the symmetric and asymmetric methods.
How a Hybrid Cryptosystem Works
The following steps show the cryptographic process for hybrid systems:
- Session Key Generation: A random symmetric key (session key) is generated.
- Key Exchange: The session key is encrypted using the recipient’s public key.
- Data Encryption: Data is encrypted using the session key.
- Decryption: The recipient decrypts the session key with their private key and uses it to decrypt the data.
Examples of Hybrid Systems
- TLS/SSL Protocols: Hybrid cryptosystems are used in TLS/SSL protocols wherein RSA or ECC is used for key exchange, and AES for bulk data encryption.
- Secure Email (PGP/GPG): Symmetric and asymmetric encryption methods protect messages and attachments.
Best Practices in Cryptography
For effective and secure cryptographic systems, users must adhere to the following best practices:
- Use Trusted Libraries: Well-established cryptographic libraries like OpenSSL or Libsodium must be used.
- Avoid Deprecated Algorithms: Deprecated and obsolete algorithms such as DES, RC4, and MD5 should be avoided as they are considered insecure.
- Regularly Rotate Keys: Key rotation policies should be in place to reduce the risk of compromised keys.
- Secure Key Storage: Private key must be stored in a secure hardware module (HSMs) or encrypted containers.
- Strong Random Number Generation: Random number generators used for key generation must be cryptographically secure.
How to Choose the Best Approach for Cryptography?
When choosing between symmetric and asymmetric approaches, specific security requirements and use cases should be considered. It is important to understand when to use symmetric vs asymmetric encryption to maintain secure communication and protect sensitive data.
Key management, computational efficiency, data size, and desired functionality are essential in selecting the appropriate method.
Three practical examples of when to use symmetric vs asymmetric encryption are:
- File Encryption: Symmetric encryption is fast and highly computationally efficient. Hence, it is the preferred approach for file encryption. Its ability to handle high volumes of data also makes it an ideal choice.
- Secure Key Exchange: Protocols like SSL/TLS use asymmetric encryption for secure key exchange, ensuring that symmetric keys can be safely shared between parties without being intercepted.
- Digital Signatures: Digital signatures are verified using public and private key pairs with asymmetric encryption.
Conclusion
For individuals working in IT, cybersecurity, or software engineering, it is crucial to understand the difference between symmetric and asymmetric cryptography. Each is beneficial on its own, but when used together, they provide a robust foundation for secure digital communications.
While symmetric cryptography is faster and more efficient for large volumes of data, asymmetric cryptography provides robust authentication and secure key exchange mechanisms. Systems should be designed to withstand evolving cyber threats, and hence, a deep understanding of both symmetric and asymmetric cryptographic systems is essential.
Finally, the choice between symmetric and asymmetric cryptography is not mutually exclusive. The best of both worlds should be capitalized to achieve performance and security.
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












