Top Skills for Becoming a Successful Ethical Hacker
|
|
In today’s digital world, there is no digital privacy, and the chances that your digital accounts will be hacked or that cyber attacks will occur are very high. Such situations make ethical hackers hold an evergreen demand.
Historically, defensive and offensive cybersecurity pursuits have been explained using the monikers of whitehat and blackhat hackers. These nicknames were used to differentiate between good and bad guys. The good guys here are the representatives of the modern cybersecurity ecosystem, and they are the ethical hackers.
So, what is ethical hacking?
Ethical hacking is an authorized attempt to gain unauthorized access to a computer system, application, or data. It is also known as penetration testing or white-hat hacking. In ethical hacking, the strategies and actions of malicious attackers are duplicated to test an organization’s defenses, and vulnerabilities are fixed.
| Key Takeaways: |
|---|
|
This article is aimed at the following topics:
|

This article outlines the educational background and the top skills required to be a successful ethical hacker.
What is an Ethical Hacker?
An Ethical Hacker or a Whitehat Hacker is a professional who performs penetration testing to test an organization’s IT security to identify vulnerabilities to cyber threats or attacks. Once these vulnerabilities are identified, the cybersecurity or IT team tries to resolve and strengthen the security.
Ethical hackers use their technical skills and knowledge to identify computer systems, applications, and network vulnerabilities. Unlike malicious or black hat hackers, ethical hackers operate by obtaining explicit permission from the organization they are testing and work within strict legal and moral limits.
An ethical hacker performs defensive tasks and improves an organization’s security posture by:
- Conducting simulated cyberattacks to test an organization’s security.
- Identifying security vulnerabilities before offensive hackers can exploit them.
- Preparing detailed reports of threats and vulnerabilities and recommendations for fixing them.
- Assisting organizations in developing robust security policies and practices.
In many ways, an ethical hacker behaves like a mystery shopper who visits retail stores incognito to spot problems and provide feedback. These mystery shoppers sometimes stage shoplifting incidents to test a store’s security.
Ethical hackers also act as cyber criminals who may attempt to trick employees into revealing sensitive information and test whether laptops and mobile devices are correctly configured, protected, and stored. An ethical hacker may also explore all possible ways a “blackhat” hacker may try to attack systems.
How to Become an Ethical Hacker
There is no standard educational criterion for an ethical hacker. Still, a Bachelor’s or Master’s degree in computer science, information security, or mathematics helps to accelerate a career in this domain. Ethical hacking also requires relevant industry-level skills to soar high in one’s career.
Ethical Hacker Education Requirements
An ethical hacker needs a strong educational foundation that can provide a solid base of knowledge and improve job prospects:
- A Bachelor’s or Master’s degree in Computer Science, Information Technology, or Cybersecurity
- Knowledge of Mathematics, Electrical Engineering, or related technical disciplines
- Some positions may prefer or require advanced degrees or specialized courses in network security, cryptography, ethical hacking, and digital forensics.
Professional Ethical Hacker Certifications
Cybersecurity is continuously evolving, and an ethical hacker is a lifelong learner. Certifications play a crucial role in demonstrating expertise and commitment to the field. These certifications are significant to employees as they validate specific skills and knowledge. Here are the key certifications for an ethical hacker:
- Certified Ethical Hacker (CEH): This widely recognized certification focuses on ethical hacking methodologies and lays a strong foundation for ethical hackers.
- Offensive Security Certified Professional (OSCP): This highly respected certification emphasizes hands-on skills.
- CompTIA Security+: This is an entry-level certification covering essential security concepts.
- GIAC Penetration Tester (GPEN): GPEN focuses on penetration testing methodologies.
- Certified Information Systems Security Professional (CISSP): This is an advanced certification for experienced professionals
- Cloud Security Certifications: Deals with cloud security. An example of this certification is AWS Certified Security Specialty.
These certifications conduct rigorous exams and practical demonstrations of skills. Apart from formal education and certifications, an ethical hacker also requires technical skills and knowledge, including networking, programming, operating systems, etc. They also need good knowledge of soft skills and ethical conduct, such as communication, problem-solving, moral judgment, etc.
How to Learn Ethical Hacking: Step by Step
To become an ethical hacker, a professional needs a formal educational background in a related field. Additionally, they need several skills to propel their ethical hacking career in the right direction. Here, we enumerate the necessary skills.
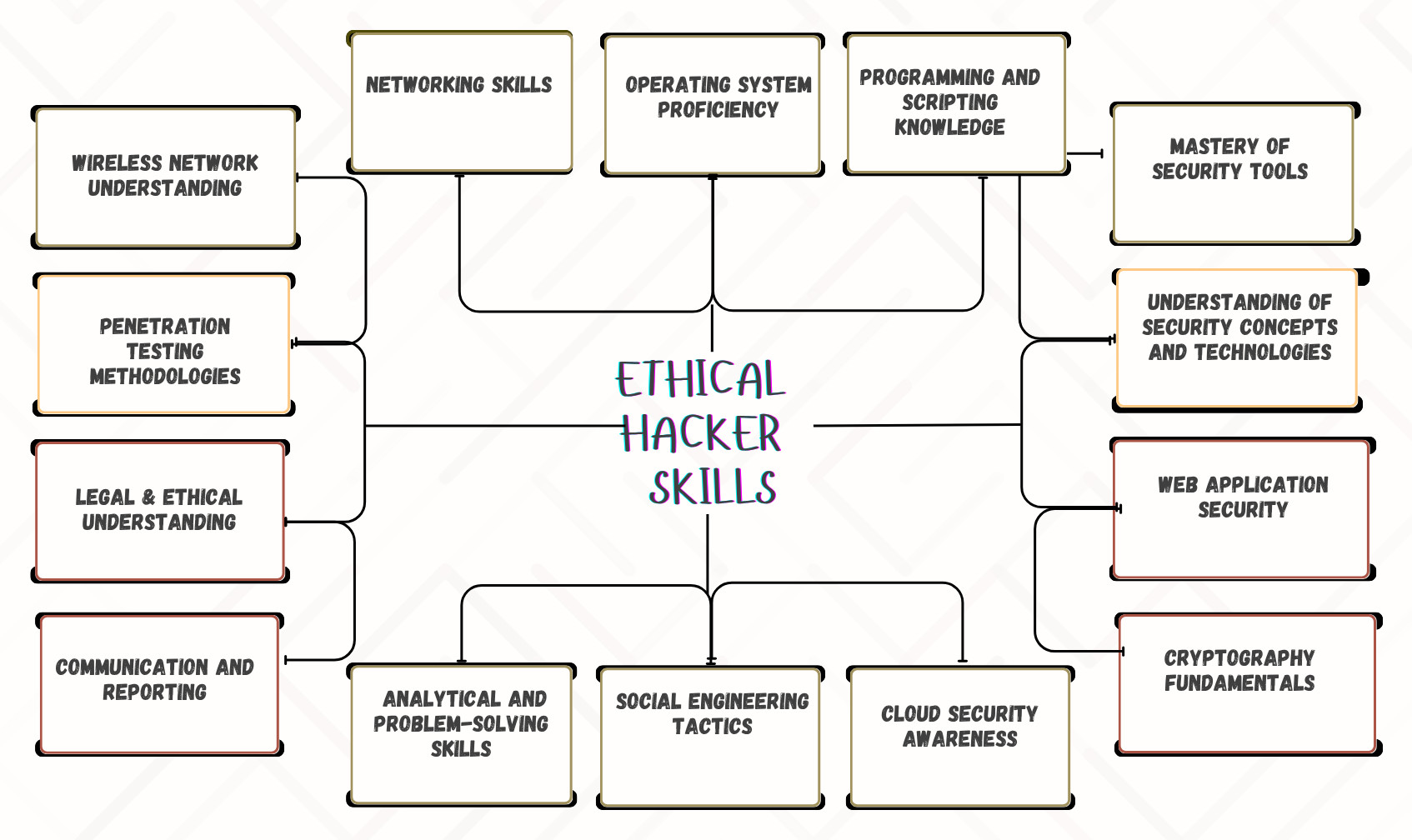
1. Networking Skills
A deep understanding of computer networks is essential for ethical hacking. An ethical hacker must understand how systems communicate, the protocols used, and where vulnerabilities may exist. An ethical hacker has to master the following key networking concepts:
- OSI and TCP/IP Models
- Standard Networking Protocols: HTTP(S), FTP, SSH, SMTP, SNMP, DNS, and DHCP
- Subnets and IP addressing
- Network devices: Routers, switches, firewalls, IDS/IPS
- Packet Analysis and Sniffing Tools: Wireshark, tcpdump
Weaknesses in network configurations are the most common points for hackers to hack into the system. Understanding the network operations and knowing how information flows and where it may be intercepted is necessary for identifying threats before attackers find them.
2. Operating System Proficiency
An ethical hacker must primarily know Unix-based operating systems like Linux, as it dominates the cybersecurity field. They must also be comfortable navigating multiple operating systems. Key skills required here are:
- Navigating and scripting in Linux (using Bash, Shell commands)
- Deep understanding of Windows and Active Directory
- Thorough knowledge of file system structures and permissions
- Managing processes, services, and logs
An ethical hacker should focus on the following tools and environments:
- Kali Linux, Parrot OS: Linux distributions focusing on ethical hacking
- Windows PowerShell: This is for writing scripts that automate tasks and analyze systems.
With internal knowledge of various operating systems, an ethical hacker can replicate the conditions under which malicious attackers act.
3. Programming and Scripting Knowledge
As an ethical hacker, a professional must write scripts and modify existing ones to bypass security defenses and automate tasks. Hence, an ethical hacker should know programming languages and scripting, including:
- Python: Widely used programming language in security tools and automation
- Bash: Unix-based shell used for scripting
- PowerShell: Used for scripting in Windows environments
- JavaScript: Exploits and tests web vulnerabilities
- C/C++: Provides memory management and low-level exploits
- SQL: Required for database-related vulnerabilities like SQL Injection
An ethical hacker does not need to be a full-time developer, but they must be code-literate enough to walk through the code to understand how applications are built and where they might break.
4. Mastery of Security Tools
Ethical hacking tools enhance the productivity and accuracy of hacking. An ethical hacker should be proficient in these security tools. The categories include:
- Network Scanners: Nmap, Angry IP Scanner
- Vulnerability Scanners: Nessus, OpenVAS
- Exploitation Frameworks: Metasploit, ExploitDB
- Password Cracking Tools: Hashcat, John the Ripper
- Web App Testing: Burp Suite, Open Worldwide Application Security Project (OWASP) Zed Attack Proxy (ZAP)
- Social Engineering Tools: SET (Social Engineering Toolkit)
- Forensics Tools: Autopsy, Volatility
A skilled ethical hacker is expected to know each tool’s specialty and how to use the right tools for enumeration, exploitation, and reporting.
5. Understanding of Security Concepts and Technologies
In addition to technical know-how, ethical hackers must understand a conceptual framework to direct their thinking. These critical concepts include:
- CIA Triad (Confidentiality, Integrity, Availability)
- Threat modeling and risk assessment
- Zero-day and known vulnerabilities
- Defense-in-depth architecture
- Encryption (SSL/TLS, AES, RSA)
- Firewalls and Intrusion Detection/Prevention Systems
Knowing how organizations secure their data, ethical hackers can grasp the entire picture and anticipate how attackers may intrude on the system.
6. Web Application Security
The maximum number of cybersecurity attacks happens on web applications. Ethical hackers must therefore understand how the web works. They should possess the following web skills:
- HTTP request/response cycle
- Web scripting, including HTML, JavaScript, cookies, and session management
- REST APIs and WebSockets
Ethical hackers should also know OWASP vulnerabilities. This is a baseline as a skilled hacker should simulate attacks, like XSS payload injections, and manipulate API requests to test a website’s defences. These top OWASP vulnerabilities include:
- Injection (SQL, Command)
- Broken Authentication
- Cross-Site Scripting (XSS)
- Insecure Direct Object References (IDOR)
- Security Misconfiguration
Read: Top 10 OWASP for LLMs: How to Test?
7. Cryptography Fundamentals
Understanding cryptography and its concepts is necessary when testing communications and stored data security. A skilled ethical hacker must have a deep understanding of:
- Hashing algorithms: MD5, SHA-256
- Symmetric and asymmetric encryption types
- Digital signatures and certificates
- TLS/SSL handshakes
- Common cryptographic attacks: brute force, padding oracle, downgrade attacks
An ethical hacker should be able to identify a weak or outdated cryptographic implementation and suggest secure alternatives.
For a more detailed article on Cryptography, read: What is Cryptography?
8. Cloud Security Awareness
Most of the modern infrastructure resides in the cloud. As more and more companies move towards cloud computing, ethical hackers must learn cloud environments in detail and acquire the skills for cloud environments:
- Understanding IAM (Identity and Access Management)
- Analyzing misconfigured S3 buckets or blob containers
- Cloud-specific attack vectors (e.g., SSRF into metadata service)
- Container security (Docker, Kubernetes), read: Containerization and Test Automation Strategies
- Auditing serverless applications
Assessing cloud infrastructure security is rapidly becoming a must-have skill in penetration testing.
9. Social Engineering Tactics
One of the weakest links in cybersecurity is humans. Hence, ethical hackers must simulate social engineering attacks to test awareness and training. For this purpose, they should be knowledgeable about the following social engineering tactics:
- Phishing (emails, SMS, fake login portals)
- Pretexting or fake identity (posing as someone trustworthy)
- Baiting (using malware-infected devices or files)
- Tailgating (physical security breach by following someone into a secure area)
Ethical hackers can opt for controlled simulations of these attacks to identify human vulnerabilities.
10. Analytical and Problem-Solving Skills
Ethical hackers must also possess analytical, problem-solving, and technical skills. Hacking is detective work and involves logic, creativity, and persistence. A skilled ethical hacker must possess the following analytical thinking traits:
- Pattern Recognition: Ability to spot anomalies in logs or traffic
- Lateral Thinking: Approach a system from an unconventional angle
- Root Cause Analysis: Trace a vulnerability back to its origin, read: Root Cause Analysis Explained
These soft skills greatly help skilled ethical hackers when tools fail or provide limited insights. Ethical hackers can use creative thinking to break through stalemates.
11. Communication and Reporting
Even if an ethical hacker successfully penetrates the system and identifies vulnerabilities, the work remains incomplete if these findings are not communicated to the respective stakeholders. A skilled ethical hacker must be able to explain what they did and why it matters, clearly and professionally.
An ethical hacker is expected to:
- Write detailed and actionable vulnerability reports
- Communicate with technical and non-technical stakeholders.
- Recommend fixes for identified flaws.
- Create executive summaries for management.
Effective communication ensures improved security.
12. Legal and Ethical Understanding
Ethical hackers are expected to strictly follow legal boundaries and always obtain proper authorization before they begin identifying vulnerabilities.
Key considerations to be given are:
- Understand the Computer Fraud and Abuse Act (CFAA)
- Follow the rules of engagement (ROE)
- Create non-disclosure agreements (NDAs)
- Protect client data confidentiality.
Crossing legal or moral lines, either intentionally or unintentionally, can have serious consequences for individuals and organizations. Hence, ethical hackers should maintain their reputation by being legally and ethically responsible. Read: AI Compliance for Software.
13. Penetration Testing Methodologies
Ethical hackers should follow a consistent, structured process to ensure comprehensive testing and reliable results.
Popular methodologies of penetration testing are:
- PTES (Penetration Testing Execution Standard)
- OWASP Testing Guide
- NIST SP 800-115
- OSSTMM (Open Source Security Testing Methodology Manual)
These testing frameworks and methodologies help standardize engagement from planning through execution and reporting. Read more about Security Testing.
14. Wireless Network Understanding
Wireless networks have become very popular in recent decades and are also vulnerable to malicious attacks, such as web attacks. Ethical hackers should have knowledge of wireless networks so that they can assess them and identify vulnerabilities that could be exploited by hackers.
Ethical hackers should know:
- Wireless Protocols: Major wireless protocols include Bluetooth, Zigbee, and Wi-Fi.
- Wireless Security: Knowledge of WPA2, WPA3, and other wireless security standards and techniques.
- Wireless Hacking: Methods such as rogue access point configuration, packet sniffing, and encryption cracking.
Conclusion
An ethical hacker is a modern cyber defender. Becoming a successful and skilled ethical hacker involves blending technical knowledge, critical thinking, and strong morals. This is not a one-time certification or a course but a mindset of curiosity, continuous learning, and a passion for helping organizations become more secure.
Ethical thinking is constantly evolving, and mastering the top skills discussed in this article helps one navigate and defend against the complex threats of the digital age.
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












