What are Communication Protocols in Engineering?
|
|
Today, engineering systems communicate globally within a fraction of a second. However, the invisible threads that weave everything together so that systems can communicate are the Internet Communication Protocols.
| Key Takeaways: |
|---|
|
This article explores the details of internet communication protocols (protocols used for communication between two devices over the internet), their importance, major types, challenges, and future trends.
What is a Communication Protocol?
A communication protocol is a standardized set of rules that enables two or more connected devices to exchange information.
The protocols determine how the data is formatted, transmitted, routed, and interpreted. The data from one device is sent to another device that processes it. Communication protocols ensure the data is correctly understood and processed regardless of differences in hardware, software, or location.
A few points to remember related to communication protocols are:
- Protocols can be perceived as the language of the internet, which provides a standardized way for devices to communicate.
- Protocols define the format, timing, and sequence of data transmission. This standardized way ensures that devices understand each other.
- In the absence of protocols, devices would be unable to interact, and communication would be impossible. For example, if there are no protocols, it will make the internet as we know it today impossible.
Why Are Communication Protocols Crucial in Engineering?
When two devices communicate and exchange data, the sender and receiver are parts of different networks, located in other parts of the world with different internet connections and data transfer rates. For this reason, a protocol is necessary to manage the flow control of data and access control of the link being shared in the communication channel.
There are several reasons why internet communication protocols are crucial in engineering:
- Network Communication Systems: Understanding Internet protocols is crucial for designing, implementing, or maintaining network communication systems, including the Internet.
- Digitization: As technologies advance, protocols evolve to meet new challenges and demands of the digital world.
- Interoperability: Diverse systems can communicate with each other regardless of their location, hardware, software, and technologies they use.
- Scalability: Protocols facilitate growth from small local networks to global systems.
- Security: Protocols help protect data integrity and privacy as they have built-in security mechanisms.
- Reliability: They ensure accurate data delivery, even across unreliable networks.
- Automation: Communication protocols support integration between various systems such as embedded systems, cloud services, and software applications.
In essence, without these protocols, the Internet and, by extension, much of modern engineering would not function the way it does today. They are the backbone of the internet, and enable seamless and reliable communication between devices across the globe.
The OSI Model and Protocol Stack
Internet communication protocols follow the Open Systems Interconnection (OSI) model. This is a conceptual framework of seven layers, with each layer serving a distinct purpose. The following figure shows the OSI model with example protocols at each layer. Since each layer performs different functions, the protocols that are implemented at each layer correspond to each layer’s function.
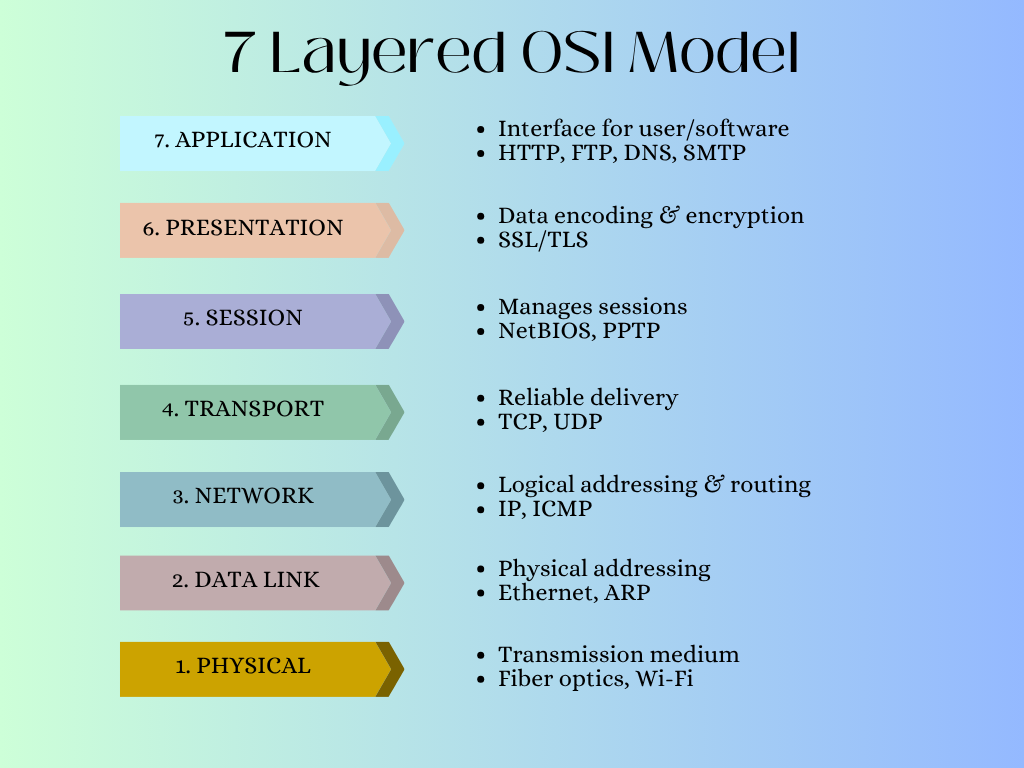
As shown in the figure, the lowermost layer is the physical layer, and the topmost layer is the application layer. The physical layer deals with hardware and physical devices. As the model progresses layer by layer, the last one, the application layer, is the actual interface or application that the user can see.
Engineering applications often span multiple layers, and they rely on this protocol stack, such as TCP/IP, which combines several protocols from these layers into a usable architecture.
What is an IP Address? How does IP Routing Work?
An Internet Protocol (IP) address is a unique identifier assigned to a machine or domain that connects to the Internet. It is a series of characters, such as ‘192.172.0.0‘. IP addresses translate into human-readable domain names via DNS resolvers, using which users are able to access websites.
When communication is initiated between two devices, an IP packet is created by adding an IP header to each packet of data before sending it across. An IP header is a series of bits (ones and zeros) and contains several information related to data packets, including the sender’s and receiver’s IP addresses. In addition, the IP header also contains:
- Header length
- Packet length
- Time to live (TTL) – the number of network hops a packet makes before it is discarded
- Which transport protocol is being used (TCP, UDP, etc)
Note: In IPv4 (version 4), there are a total of 14 fields for information, with one field being optional. IPv6 is the newer version of IP and has many more characters and thus more permutations.
IP routing is the process of forwarding IP packets from a source to a destination across one or more networks. The key device in this process is Routers, which use routing tables to determine the best path for a packet to travel, based on the destination IP address. The process is shown below:

Here, the sender and receiver are identified by the IP address. When the sender sends IP packets, they contain both the sender and receiver IP addresses.
Routing tables contain information about network paths and destinations, including next-hop addresses and metrics indicating the cost of reaching each destination. Based on this data, they decide the best path the packet can take to reach the destination.
Standard Communication Protocols in Engineering
Here, we discuss the most widely used and engineering-relevant communication protocols.
Internet Protocol (IP)
IP is a fundamental protocol that assigns unique addresses (IP addresses) to devices communicating over the network and routes data packets across the network.. IP is like an address system for the internet, ensuring the data is delivered to the correct destination.
There are two main versions of IP: IPv4 and IPv6. IPv4 is the most widely used version, though IPv6 is also used, but is not very popular.
IP is foundational to all internet-based communications, including web, cloud, and Internet of Things (IoT) systems. Read: IoT Automation Testing Guide: Examples and Tools.
Transmission Control Protocol (TCP)
TCP establishes a connection between devices, verifies data integrity, and retransmits lost packets. It ensures reliable and ordered data delivery with acknowledgments. TCP works with IP closely to ensure that data packets arrive in the correct sequence and are not corrupted during transmission.
The process of TCP/IP transmission is shown below:
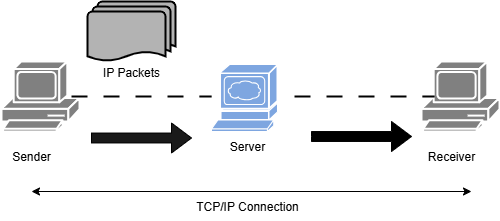
TCP/IP is the primary protocol and is used everywhere, including web browsing, file transfers, and remote logins.
User Datagram Protocol (UDP)
UDP is one of the core protocols of the Internet Protocol (IP) suite. It is a communication protocol that sends data without error checking or delivery confirmation. Unlike TCP, UDP is connectionless and does not guarantee delivery, order, or error checking. UDP is a lightweight and efficient option in certain cases, such as time-sensitive transmissions, such as video playback or DNS lookups.
Hypertext Transfer Protocol (HTTP/HTTPS)
HTTP/HTTPS is a foundation for transferring web pages and other resources (hypertext) to the World Wide Web (WWW). HTTPS is a secure version of HTTP and uses SSL/TLS encryption to protect data transmitted between a web browser and a server.
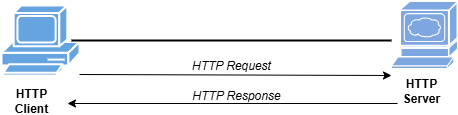
The process of HTTP communication over the web is shown in the figure above. An HTTP client connects to the HTTP server for hypertext transfer. A web page opens on client machine requests for data from the server which is sent back as a HTTP response.
File Transfer Protocol (FTP/SFTP)
FTP is used to transfer files between systems over a network. SFTP is a secure variant of FTP using SSH. The process of file transfer between the Client and the FTP server is shown below:
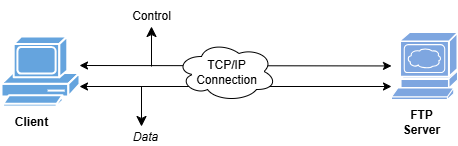
FTP is a client-server model and operates over a TCP/IP connection. The client requests a file from the server, which the server transfers to the client. Before placing a request, a connection has to be established between the client and the FTP server using login credentials. FTP is mainly used for firmware updates and data backups from embedded systems.
Domain Name System (DNS)
DNS translates the human-readable domain names (such as testRigor.com) into their numerical IP addresses that computers can use to identify each other. DNS is used in systems that dynamically connect to cloud resources.
When a user types a website address like ‘www.testrigor.com’ into the browser, the computer needs to find the corresponding IP address to connect to the website’s server. DNS resolves this by looking up the domain name in a vast, distributed database of records.
Simple Mail Transfer Protocol (SMTP)
SMTP is a standard protocol for sending outgoing emails. The protocol uses the header of the mail to get the email id of the recipient and enters the email into the queue for outgoing emails.The moment the email is delivered to the recipient’s email address, it is removed from the outgoing list. The email may have text, video, image, etc. SMTP helps in setting up some communication server rules.
SMTP acts as the backbone for email transmission, enabling mail servers and other message transfer agents to send, receive, and relay email messages.
Simple Network Management Protocol (SNMP)
SNMP is a widely used protocol for monitoring and managing network devices. Administrators use SNMP to collect information about network devices, such as routers, switches, and servers, and it also allows them to make some configuration changes remotely. It is an application-layer protocol that operates within the TCP/IP suite and utilizes UDP ports 161 and 162.
SNMP is used to manage switches, routers, or networked industrial equipment.
Message Queuing Telemetry Transport (MQTT)
MQTT is a lightweight messaging protocol with a publish/subscribe model. It is used in low-bandwidth, high-latency, or unreliable networks.
It is commonly used in IoT devices, home automation, and industrial telemetry.
WebSocket
A WebSocket is a communication protocol that provides full-duplex, bidirectional real-time communication between a client and a server over a single, persistent TCP connection. Unlike HTTP, which follows a request-response model, WebSockets enable real-time, continuous data exchange. This protocol is used in applications that need low-latency, two-way communication, such as chat applications, online games, and live dashboards.
Protocols in Engineering Contexts
The engineering field operates across many domains, including mechanical, civil, electrical, software, and beyond. Internet communication protocols are used in each domain to bridge the gap between physical systems and digital intelligence.
The following table lists the protocols used in major engineering domains:
| Engineering Domain | Protocols Details | Examples |
|---|---|---|
| Embedded Systems & IoT |
|
|
| Cloud-Based Systems |
|
|
| Industrial Automation |
|
|
| Software Engineering |
|
|
| Smart Grids and Infrastructure |
|
Communicating between control centers and field devices in utility networks. |
Challenges in Internet Protocol Implementation
There are various challenges the professionals face in Internet Protocol implementation:
- Latency Sensitivity: Real-time systems, such as remote surgery, robotics expect protocols with minimal latency. The ideal solution for this is to use low-latency protocols like UDP.
- Bandwidth Constraints: Sometimes applications like IoT or remote devices operate under limited connectivity. In such cases, using lightweight protocols such as MQTT helps.
- Interoperability: Using diverse hardware/software stacks in a system can give rise to compatibility issues and thus affect interoperability. Systems should follow open standards, use abstraction layers, or protocol bridges to mitigate this issue.
- Scalability: Systems must be scalable and able to accommodate a growing number of devices or users. Designing systems using scalable cloud services and stateless protocols like REST can help with scalability. Read: Software Scalability – A Complete Guide.
Trends and Future Directions
Here are some of the emerging trends and future directions for internet communication protocols:
- Quick UDP Internet Connections (QUIC) Protocol: Developed by Google, this transport-layer network protocol is designed to be a faster, more secure alternative to TCP for web traffic. QUIC incorporates features like built-in security (TLS), speedier connection establishment, and improved performance through multiplexing and congestion control.
- 5G and URLLC (Ultra-Reliable Low Latency Communication): This enables a range of critical applications that require high reliability and near-instantaneous data transmission (protocols that handle < 1ms latency). This is primarily used in autonomous vehicles, traffic control systems, robot control, and drone communications.
- Protocols for Edge Computing: To shift from cloud to edge computing, protocols that support distributed architectures are required. Protocols like MQTT-SN and LwM2M have a good scope.
- AI-Assisted Protocol Optimization: Machine learning is now used for congestion prediction, routing optimization, and auto-tuning of protocol parameters.
Conclusion
Communications protocols form the nervous system of engineering systems in this digital age. These protocols enable intelligent, connected, and scalable engineering systems and help them send a simple HTTP request to manage a complex network of IoT devices.
Understanding communications protocols empowers engineers to build reliable, secure, and future-ready systems. As we leap into the world of 5G, AI, and edge computing, mastering these protocols will be advantageous and essential.
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












