Authentication vs. Authorization: Key Differences
|
|
Security is paramount in today’s highly digital world. As individuals, businesses, and governments rely on technology for their day-to-day activities and everything from banking to healthcare and education to communication, two core pillars of security, authentication and authorization, have become critical. They are critical for secure digital system access.
This article explores the authentication and authorization processes and the key differences between the two.
| Key Takeaways: |
|---|
|
What is Authentication?
Authentication is verifying and confirming a user’s identity, a device, or an application. It is the first step in the security process and ensures that the entity is who or what it claims to be. In the authentication process, the key question is “Who are you?”
When this question is correctly answered, the authentication process verifies the entity’s identity and releases a session token for using the device or application for which the identity was verified.
Purpose
The main objective of authentication is identity verification. The authentication process confirms the identity of the user, system, or process trying to gain access to the system, network, database, or application.
Authentication Example
A classic example of authentication is logging into a website using a username and a password. From email services like Gmail and Outlook to retailers like Amazon and Flipkart, all use an authentication process to grant users access.
Types of Authentication
The following are some of the standard authentication methods used:
- Password-based authentication is the most common and oldest authentication method. A username and password are required to authenticate. If the password matches the password created by the user or the system, the system assumes it is a valid user and grants access.
- A One-time PIN (OTP) or temporary password is generated by the system. OTP allows a user access to a single or temporary session that expires after a set amount of time. This method is typically used in mobile banking systems, where users are asked to provide OTP for banking transactions like money transfer in addition to login information.
- Multi-factor authentication (MFA) combines two or more verification methods (e.g., password + OTP). Two-factor authentication (2FA) and multi-factor authentication (MFA) are also increasingly used to enhance security beyond the level provided by passwords alone. One or more modalities must be successfully verified before access to the system is granted. For example, MFA could ask a user to provide a security PIN from an authenticator app in addition to a password to access any system.
- Biometric authentication uses biometric entities like fingerprints, facial recognition, or retinal scans for authentication. This is supposed to be the most secure method, as biometric factors are unique to every individual. The access systems in organizations mostly use biometric authentication to allow entry for people in the company.
- Token-based authentication involves digital tokens like JWT (JSON Web Tokens) to verify identity. The entity trying to access the system or a device must authenticate itself by presenting the token.
- Single Sign-On (SSO) enables users to authenticate once and gain access to multiple applications. Web applications mostly use SSO authentication.
How Authentication Works
Authentication is based on the exchange of user credentials or authentication factors, which are used as evidence to verify the user’s identity. The authentication process involves several steps, depending on the method used. However, the general sequence of steps is shown below.
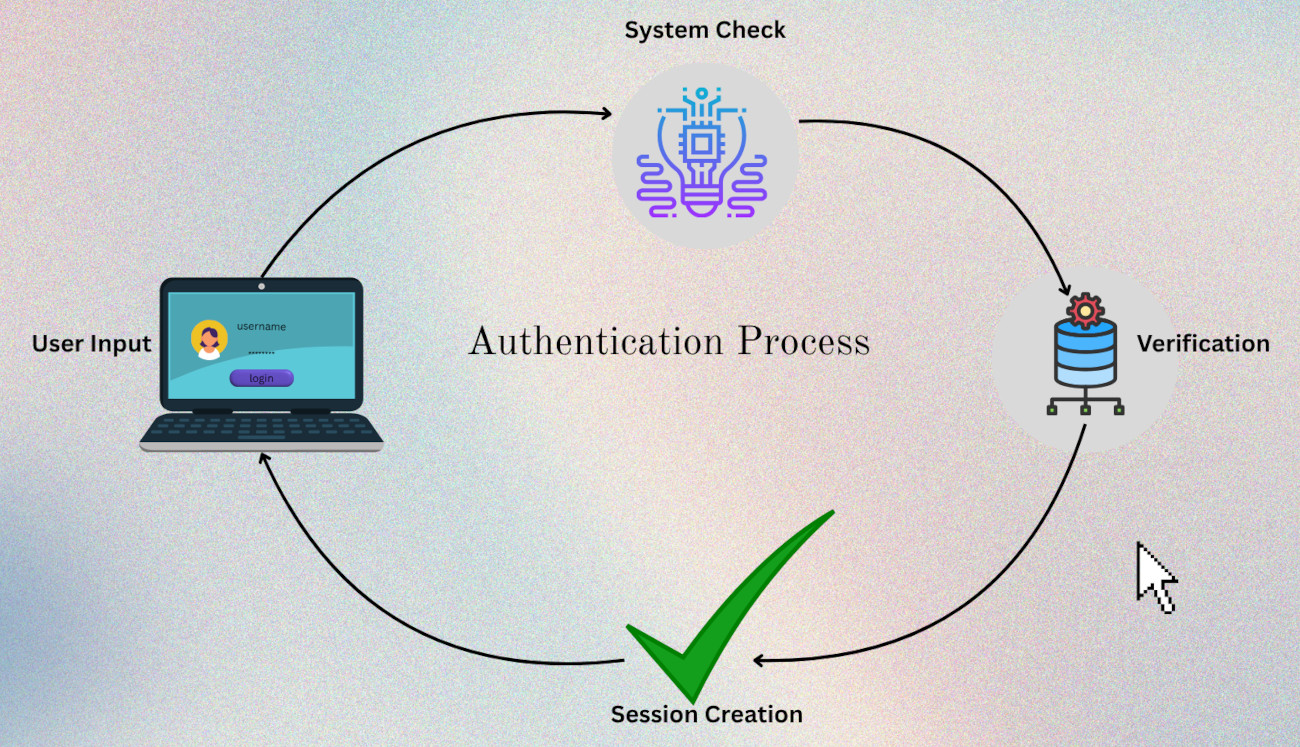
A general overview of how password-based authentication works is as follows:
- User Input: The user provides credentials for authentication. Generally, username/email and password are provided as credentials.
- System Check: The system checks the credentials against stored data. The combination of username and password is usually stored in the database of the system being authenticated.
- Verification: The user is authenticated if input credentials match those stored in the system.
- Session Creation: A session token or cookie is created to maintain authentication for subsequent requests. The system also sends an appropriate response by granting login access to the user.
When a user registers with a system for the first time, a set of authentication factors is established and stored securely by the system. These factors are presented by the user at the time of login. The system then validates these factors against the ones it has stored. If they match, the system confirms the user’s identity and trusts that they are valid.
Common types of authentication factors include:
- Knowledge Factors: Only the user knows about this factor, such as a password, a PIN, or a security question.
- Possession Factors: This factor is possessed only by the user. For example, an OTP is sent to the user’s personal mobile through SMS or a physical security token.
- Inherent Factors: Biometrics, such as facial recognition and fingerprint scans, are unique to every individual.
Different applications and resources may have their own authentication systems. Many organizations also have integrated systems, such as an SSO solution like the ChatGPT app. Here, users can authenticate once to access multiple resources securely.
Some of the common authentication standards include Security Assertion Markup Language (SAML) and OpenID Connect (OIDC). SAML is XML-based standard and uses XML messages to share authentication information between systems, while OIDC uses JSON Web Tokens (JWTs) called “ID tokens.”
What is Authorization?
Authorization is the process of granting a user permission to access a physical location or an information-based resource such as a document, database, application, or website. It determines what an authenticated user is allowed to do.
Authorization usually answers the key question: “What are you allowed to do?” or “What access rights do you have?”
Authorization is often used synonymously with authentication; however, both are different terms. Authentication always precedes authorization. Users must prove their identities before a system grants or denies them rights to access resources based on predefined rules and permissions associated with their identity.
Purpose
The main objective of authorization is access control. It determined what resources or actions a user should be granted to access after they have been successfully authenticated.
Authorization Example
For example, you have logged in to Gmail. You are taken to your inbox. But if you try to access other users’ inboxes using your Gmail ID, you will get a “No Authorization” message. This means you are authorized only to access your Gmail inbox using the credentials you provided.
Similarly, when you log in to a banking system, you are only shown your own account details. You are not allowed to access another person’s account.
Hence, when a user is successfully authenticated, the authorization process grants that user specific privileges. The user cannot access any other resources beyond the ones that are authorized.
A cloud-based system like Google Cloud Platform (GCP) may allow various role-based authorizations, such as:
- Admins to create, edit, delete, and share documents.
- Editors to create and edit, but not delete.
- Viewers are only allowed to read documents.
This may be enforced at the application and resource level.
Types of Authorization
Authorization supports various models based on roles, attributes, and so on. Here are the main models:
- Mandatory access control (MAC) systems provide centrally defined access control to all users. Access is typically based on set clearance levels or trust scores. MAC is mostly used in operating systems, where it controls program access to sensitive system resources.
- Discretionary access control (DAC) systems allow resource owners to set their own access control rules. They are more flexible than MAC’s blanket policies.
- Role-based access Control (RBAC) assigns permissions based on roles (admin, dba, user, etc. ). RBAC uses predefined roles and privileges, assigns users to roles, and configures a system so that only specific roles can access each resource.
- Attribute-Based Access Control (ABAC) grants access based on user attributes (e.g., location, time) in a policy-based manner. It uses attributes, which can be attached to a user, a resource, an object, or an entire environment. If all attributes defined in the policy are true, an entity is authorized.
How Authorization Works
The authorization process is based on user permissions. Permissions are policies or rules in a system that determine what a user can access or do in a system. Once a user is authenticated, authorization decides what they can access. The process of approval is shown here:
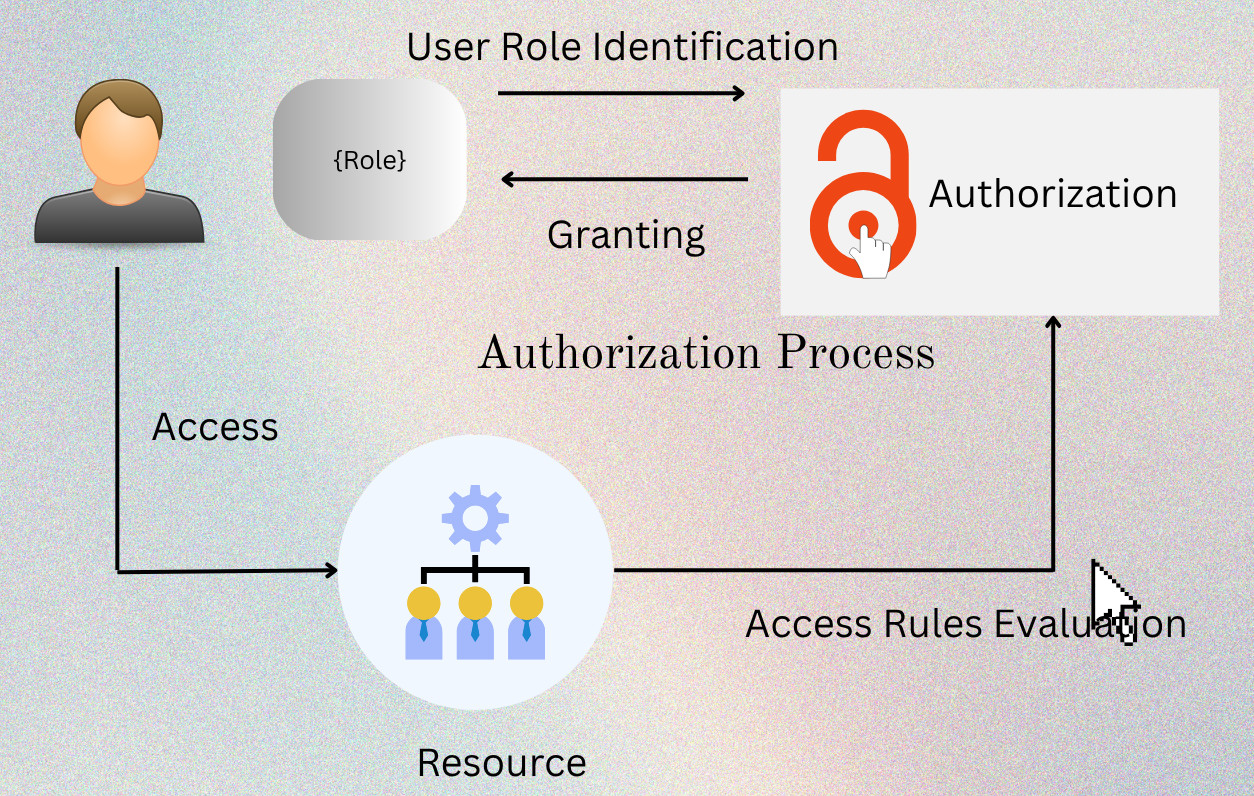
The steps shown in the figure are summarized as follows:
- User Role Identification: The System determines the authenticated user’s role as admin, viewer, editor, etc.
- Access Rules Evaluation: Depending on the role or attributes identified for this user, the system consults authorization policies to check which resources should be granted access.
- Permission Granting: The system grants or denies access to resources or functionalities depending on the authorization response.
Permissions are usually defined by administrators and security leaders and then enforced by authorization systems. When a user tries to access a resource or perform an action, authorization systems check if they have the appropriate permissions before allowing them to proceed.
OAuth 2.0, a common authorization protocol, uses an access token to delegate permissions to users. Using OAuth, apps can share data with each other. For example, OAuth enables a social media website to scan a user’s email for people the user knows, provided the user consents.
Difference Between Authentication and Authorization
The following figure depicts the difference between authentication and authorization:
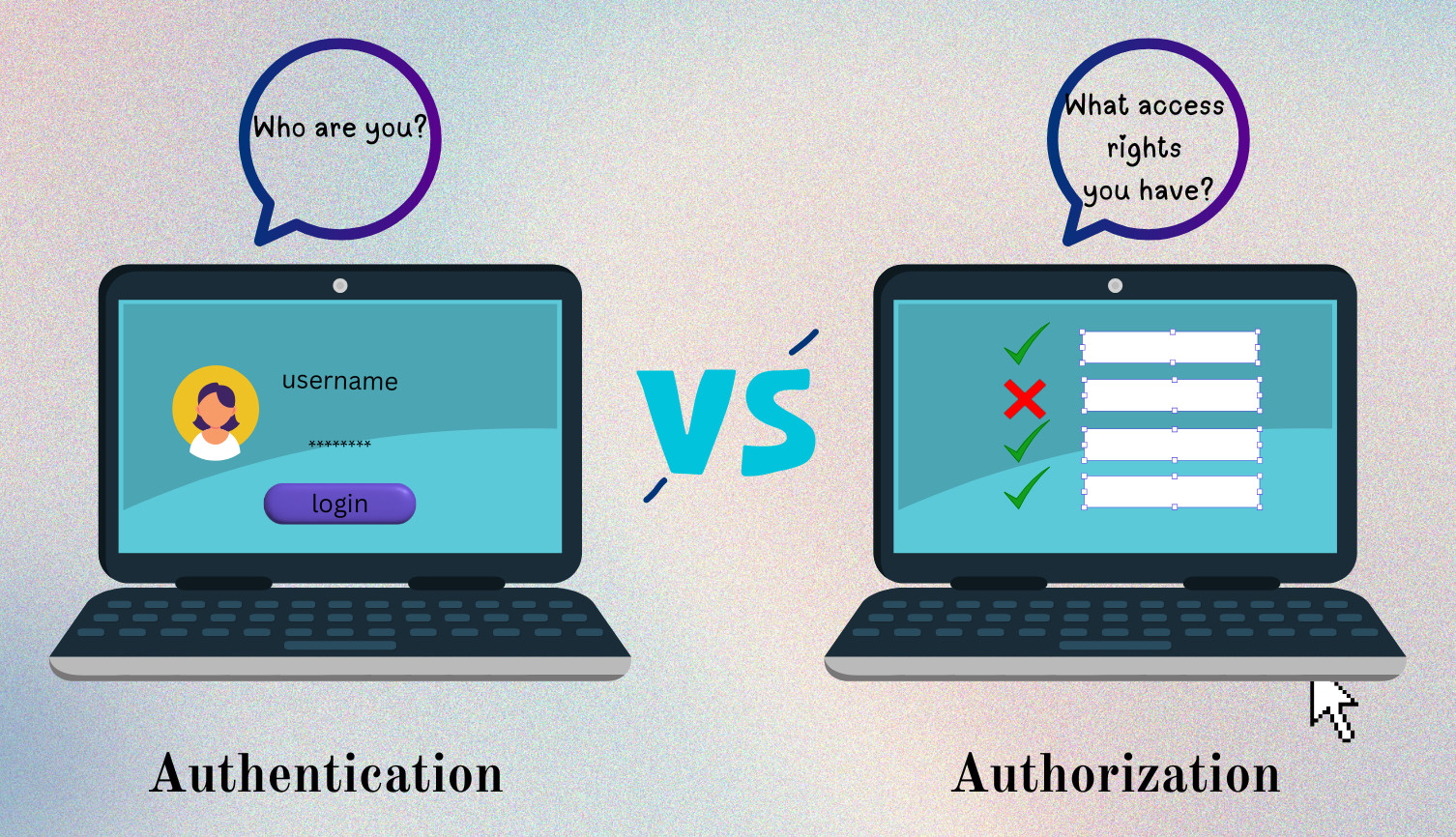
The key difference between authentication and authorization is summarized in the following table:
| Feature | Authentication | Authorization |
|---|---|---|
| Definition | The process of verifying user identity before granting them permission to access resources. | Process of verifying the user’s access level to resources. |
| Purpose | Verify identity and determine if the user is who he/she claim to be. | To determine whether to grant or deny access to the authenticated user. |
| Occurs | Before authorization | After authentication |
| Based On | User credentials (username/password, etc.) | Permissions and access rules |
| Question Answered | Who are you? | What can you do? |
| Visibility | visible to users | Often invisible to users, performed in the background |
| Data Involved | Login credentials, OTP, PIN | Access control lists, roles, policies |
| Outcome | Identity verified successfully | Access to resources is granted |
| Protocol/Framework | Governed by the OpenID Connect (OIDC) protocol | Governed by the OAuth 2.0 framework |
| Token Type | Data transmitted through an ID Token | Data transmitted through an Access Token |
| Example | Employees in a company are required to authenticate through the network before accessing their company email. | After an employee successfully authenticates, the system determines what information the employees are allowed to access. |
Which Comes First, Authentication or Authorization?
There has always been confusion, or rather a debate, regarding what comes first: authentication or authorization.
Authentication and authorization can be understood with a real-world example. When you go through the security check at an airport, you show proof of your identity to authenticate your identity. With this authentication, you can enter the airport. Then, when you arrive at the gate, you have to present your boarding pass to the flight attendant so that they can authorize you to board the flight.
So, in the beginning, authentication verifies the entity, and then authorization verifies its rights. Also, authentication and authorization both rely on identity. So, one has to identify the user first before authorizing them. Thus, naturally, authentication always comes before authorization. Once authentication verifies identity, authorization can grant privileges and access to the user as per the role.
Authentication and authorization work together seamlessly, making them appear like a single mechanism. The two components are part of an organization’s access management system, which controls, tracks, monitors, and manages users and system resources.
Real-World Authentication and Authorization Examples
Here are some real-world examples showing how authentication and authorization play a part:
-
Online BankingSecurity is paramount in the online banking system. Users access their own accounts to perform transactions such as fund transfers, view balances, invest, etc. Authentication and authorization are critical in online banking.
- Authentication: User logs in with account number and password.
- Authorization: The user has access to his/her own account and its related services and data, which enables him/her to perform various activities related to the bank account. However, the user does not have access to another person’s account.
-
Corporate NetworkAny organization’s corporate network is accessible to its employees and other users. While other users are provided minimal access to the corporate website as guests, employees can access it depending on their role in the organization or department they represent.
- Authentication: Employees log in to the corporate website with their ID badge and fingerprint.
- Authorization: They get access to relevant files and systems based on their department.
-
SaaS Application (e.g., Netflix)Any SaaS application, such as Netflix, provides access to those who have subscribed to it through its various plans. You can watch various TV shows and movies online, without having to download or store them locally.
- Authentication: Users log in using an email/password combination.
- Authorization: Once you are authenticated and logged in, Netflix’s authorization system determines what content and features you can access. This is based on your subscription plan and profile.
Authentication and Authorization in Modern Technologies
The following table shows modern technologies that authentication and authorization use:
| Technology | Description |
|---|---|
| OAuth 2.0 |
OAuth 2.0 is an industry-standard authorization protocol.
It is commonly used when third-party applications need limited access to user data.
Authentication: Performed through OpenID Connect (OIDC) layer on top of OAuth.
Authorization: OAuth issues access tokens after validating the user and their permissions.
|
| JWT (JSON Web Tokens) |
JWTs securely transmit information between parties, often containing authentication and authorization claims.
Includes user identity, roles, and expiry time.
Often used in RESTful APIs.
|
| Active Directory & LDAP |
Used in enterprise environments.
Authentication: Managed by Active Directory or LDAP servers.
Authorization: Through group memberships and security policies.
|
| IAM Solutions (Identity and Access Management) | Vendors like Okta, Auth0, and Azure AD provide centralized platforms for managing authentication and authorization. |
Authentication and Authorization Challenges
Authentication and authorization face various challenges:
- User Experience vs. Security: Since both authentication and authorization are important processes, balancing security and ease of use is a constant challenge. While complex processes can frustrate users, leniency may introduce threats.
- Misconfigured Authorization: If authorization has improper access control policies, it can result in data leaks, privilege escalation, or compliance violations.
- Session Hijacking: Authentication tokens should be adequately secured to protect sessions from hijacking.
- Dynamic Environments: Dynamic roles and microservices in dynamic environments like cloud-native applications complicate authentication and authorization processes.
- Regulatory Compliance: Authentication and authorization practices should strictly be aligned with regulatory standards such as GDPR, HIPAA, SOX, and PCI DSS.
Testing Authentication and Authorization
You’ll see authentication and authorization being a part of most modern websites. While these implementations are quite well-managed, it is important to periodically review and check their effectiveness. Various types of testing can help you with this. For example, security testing can cover use cases particular to these implementations. Testers try to:
- Bypass the login process using techniques like brute-force attacks on passwords, SQL injection, or session hijacking.
- Check if they can access resources or perform actions they aren’t supposed to, once they are authenticated. For example, a tester with a standard user account would try to access an admin-only page or modify another user’s data.
Apart from this, functional testing can also help. Testers can check if:
- The login and logout functions work as expected. They check if valid credentials grant access, and invalid credentials are rejected with the correct error messages.
- Different user roles have the correct level of access. For instance, they’d test that an administrator can see all reports, while a standard user can only see their own.
End-to-end and regression tests also inevitably cover login functionality and role-based access checks. For example, an administrator logs into their account to approve requests.
While you can do these types of tests manually, it is advisable to utilize test automation tools. You can find many tools that specialize in security, functional, and end-to-end testing. testRigor is one such tool that can simplify your end-to-end, functional, regression, and UI testing across different platforms (web, mobile, desktop) and browsers. Since it uses generative AI, it allows testers to use plain English to write tests. You can write tests that integrate with CI/CD pipelines and databases to achieve continuous testing. Here is a great example of how testRigor can simplify this type of testing – SSO Testing with testRigor
Conclusion
Authentication and authorization are considered security pillars of any application. Due to how seamless they’ve become with modern technology, many tend to assume that they’re a single process. However, they play distinctly different roles in system protection. Authentication is all about proving who you are, and authorization validates what you are allowed to do.
Working seamlessly together, they form a robust security model to ensure only valid users can access the appropriate resources. In a world of increasing threats and attacks, organizations must invest in modern, scalable, and secure authentication and authorization mechanisms to protect sensitive information and ensure compliance, trust, and business continuity.
Additional Resources
- What is Security Testing?
- How To Test for SQL Injections – Guide
- Cybersecurity Testing: Impact of AI
- The Significance of Cybersecurity in Software Development
- What is Cryptography?
- Cryptographic Algorithms: Symmetric vs. Asymmetric
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












