The Significance of Cybersecurity in Software Development
|
|
As the world is digitized, software systems have become the backbone of modern businesses, economies, and societies. However, with technological advancements comes a growing threat landscape. Malicious attacks, unauthorized access, and data breaches have become major security concerns in the software world. As cyberattacks become more frequent, damaging, and sophisticated, cybersecurity is no longer an option but a critical necessity.
| Key Takeaways: |
|---|
|
In this article, we will discuss the following:
|
This article provides an overview of cybersecurity in software development and its importance. It discusses cyber threats, defenses, and the consequences of neglecting cybersecurity.
What is Cybersecurity?
According to the Cybersecurity and Infrastructure Security Agency (CISA), the definition of cybersecurity is:
Cybersecurity is the art of protecting devices, networks, and data from unauthorized access or criminal use, and ensuring data integrity, availability, and confidentiality.
Cybersecurity gained prominence in the 1970s and was defined as a practice to protect computer systems and networks from unauthorized access, theft, or damage. Since then, cybersecurity and its developers have made great strides, and its scope has expanded to protect all aspects of digital information, including data, networks, software, and hardware.
Cybersecurity is a set of practices and protocols that protect systems by implementing security measures, such as firewalls, encryption techniques, and authentication methods. This, in general, involves the following elements:
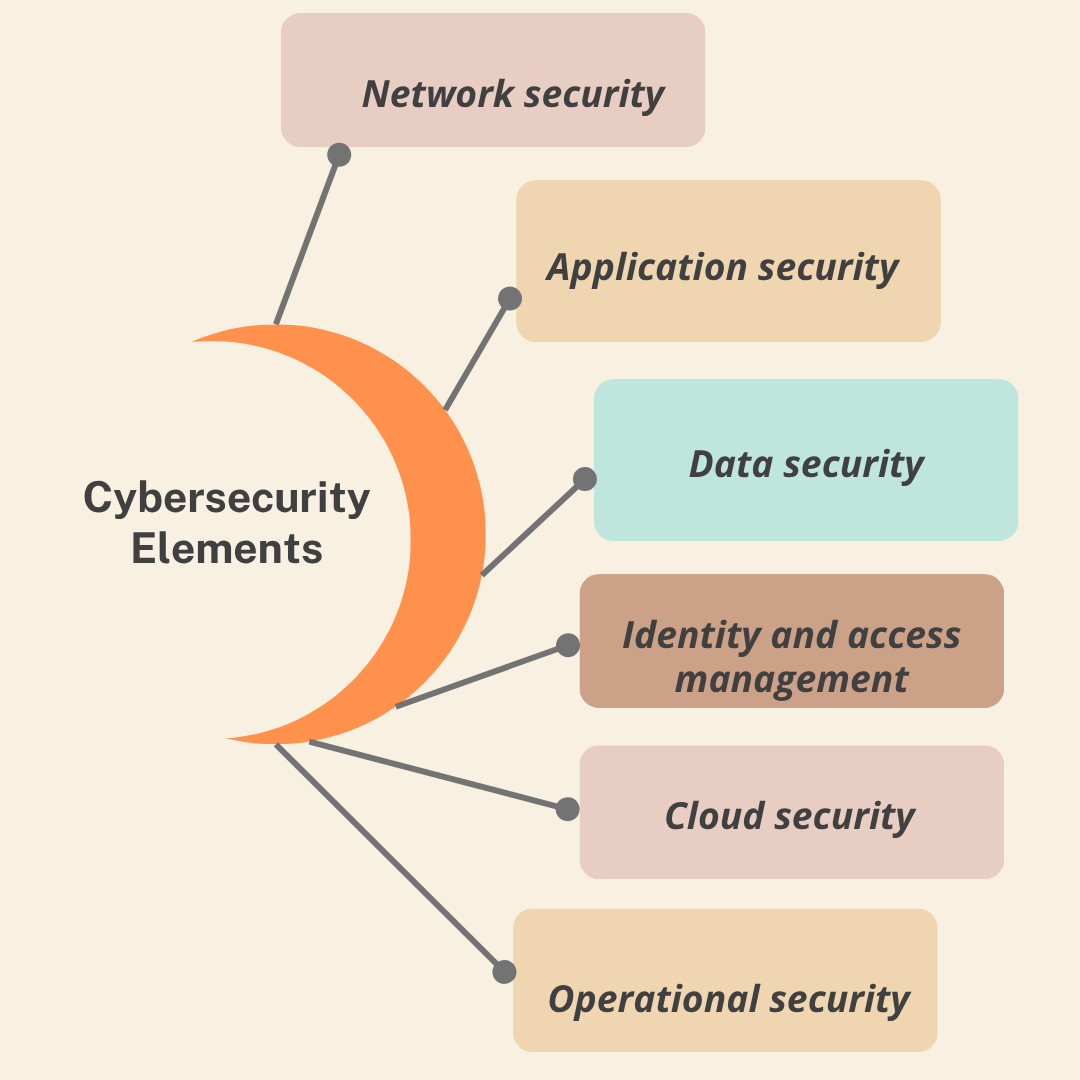
| Cybersecurity Elements | Details |
|---|---|
| Network security | Includes protecting networks, computers, and data against malicious attacks. |
| Application security | Security measures in software applications are used to protect them against malicious attacks. |
| Data security | Security measures to protect data include encryption and authentication methods. |
| Identity and access management | Security measures to protect user information, such as passwords and biometric data. |
| Cloud security | Security measures to protect cloud-based systems include security protocols and access control. |
| Operational security | Security measures taken to protect the overall security of a system include security patching and security awareness training. |
Cybersecurity in Software Development: Threats and Defenses
The threats faced continuously evolve, as do the defenses deployed to counter these threats. The following table presents these threats and defenses to overcome them.
| Cyber Threats | Cyber Defenses |
|---|---|
Malware
|
Firewalls
|
Phishing
|
Antivirus Software
|
Ransomware
|
Encryption
|
Social Engineering
|
Intrusion Detection Systems (IDS)
|
DDoS Attacks
|
End-User Education
|
Man-in-the-Middle (MITM) Attacks
|
Two-Factor Authentication (2FA)
|
These threats and defenses make us understand the complex nature of the cybersecurity landscape. Hence, remaining vigilant, adhering to best practices, and employing robust security measures are all essential in maintaining security in the face of these challenges.
Importance of Cybersecurity in SDLC
Implementing cybersecurity measures in software development environments is crucial on many occasions. Here are some of these reasons:
1. Protection of Sensitive User Data
Security breaches often result in unauthorized access to user data. Software applications handle extensive volumes of data that may be sensitive and confidential. Safeguarding sensitive data is essential to maintaining user trust. The risk of data compromise can be significantly reduced by implementing stringent measures and protecting users’ privacy. Read about Security Testing.
2. Early Identification of Cyber Threats
Cyberattacks continue to develop and become more advanced and sophisticated. To counter this, there is a growing need to follow a proactive and all-encompassing approach to security. Integrating cybersecurity into the SDLC helps identify and address the potential threats early on, reducing the risk of attacks.
3. Availability and Reliability
A software application’s reliability and availability are ensured when cybersecurity measures are implemented. Measures like protection against DDoS attacks, proactive monitoring, and robust infrastructure ensure uninterrupted software access with minimum downtime and enhanced user satisfaction.
4. Preserving Software Integrity
Unintended modifications or malicious tampering with code can compromise an application’s reliability, stability, and functionality. Preserving the integrity of software applications is a crucial aspect of software development. Integrating cybersecurity measures throughout the SDLC can provide users with a trustworthy and dependable product.
5. User trust & Brand Reputation
A security breach, however minor, can erode user confidence and damage an organization’s reputation. On the other hand, integration of cybersecurity practices in SDLC can help establish and maintain user trust. Organizations must prioritize robust security measures, demonstrate their commitment to protecting sensitive information, and establish trust, credibility, and long-term customer loyalty.
6. Maintaining Business Continuity
A security breach disrupts business operations, resulting in revenue loss and application downtime. Effective cybersecurity measures can maintain business continuity and ensure the smooth and continuous functioning of software applications.
7. Industry Regulations and Standards
Adherence to industry regulations and standards is essential for organizations. Many industries also require compliance with specific cybersecurity standards. Adherence to these standards and regulations during software development helps prevent legal issues and fines. Integrating cybersecurity practices into software development also encourages a culture of responsible data management and privacy. Read: AI Compliance for Software.
Let us have a Secure Development Lifecycle (SDL)
Every stage in the SDLC is susceptible to cyber threats. Hence, it is essential to integrate cybersecurity in each stage of software development to build inherently secure software. A Secure Development Lifecycle integrates security practices into every phase of the SDLC, from planning to maintenance. Here is how this is done:
- Requirements Phase: In the first phase of SDLC, all the security requirements should be defined along with the functional requirements. A threat modeling should be conducted to identify potential threats and vulnerabilities the application may face.
- Design Phase: This is a conceptual phase in SDLC, and security must be a prime consideration at this stage. Developers should consider potential threats to minimize vulnerability. For example, user authentication and data encryption should be considered at this stage. Similarly, architecture patterns should be secured, and attack surface analysis performed.
- Development/Implementation Phase: Developers must enforce secure coding practices during the development stage to prevent common security issues like SQL injection and cross-site scripting (XSS). Third-party libraries used should be safe. Also, using version control systems can track changes, detect anomalies, and recover from alterations due to potential security breaches. Read: How To Test for SQL Injections.
- Testing Phase: The testing phase should encompass security testing, which is critical to detecting software vulnerabilities. This includes penetration testing, vulnerability scanning, and security auditing. Potential security issues must be identified and fixed before deploying the software.
- Deployment Phase: The deployment stage involves transitioning the application from a development environment to a live environment. At this stage, proper access controls like firewalls should be in place to prevent unauthorized changes to the software. Vulnerability scans should be automated in CI/CD pipelines. Security measures such as IDS can also help quickly identify and respond to security breaches.
- Maintenance and Monitoring: The software application’s security should be continuously updated to address new threats and vulnerabilities. During this phase, measures like regular security patch updates, system updates, continuous monitoring, and security audits are essential. Read: Understanding Test Monitoring and Test Control.
Building secure software is easier than fixing security issues later. By incorporating cybersecurity practices in all SDLC stages, not only software but also the users are protected, and the brand reputation is upheld.
Read: Top 10 OWASP for LLMs: How to Test?
Key Security Principles for Developers
In addition to integrating cybersecurity practices in SDLC phases, developers should also follow these key security principles:
- Principle of Least Privilege (PoLP): According to PoLP, every module or user should have the minimum level of access necessary to perform their task. Doing this minimizes the coverage of a potential breach.
- Defense in Depth: Developers should implement layered security to ensure that even if one defense is breached, others remain intact. The security layers include:
- Network firewalls
- Application gateways
- Authentication systems
- Encryption layers
- Input Validation and Sanitization: The most common cause of security breaches is improper handling of user input. All inputs should be validated and sanitized to prevent injection attacks and other exploits.
- Authentication and Authorization: A strong authentication mechanism, like multi-factor authentication (MFA) should be implemented. For secure identity management, methods like OAuth 2.0 and OpenID Connect must be used. Read: How to do SMS, 2FA, and phone call testing using testRigor?
Best Practices for Cybersecurity in Software Development
Developers should adopt the following best practices when incorporating cybersecurity in software development.
- Secure by Design Approach: This approach is the first step towards incorporating cybersecurity into software development. It involves integrating security risk management into every stage of software design and development instead of considering it at the end.
- Continuous Testing and Auditing: The software is tested and audited to ensure real-time data security. This allows developers to identify threats and vulnerabilities before cyber criminals.
- Vulnerability Patching and Regular Updates: The rapid evolution of cyber threats necessitates continuous vulnerability patching and regular updates. Staying updated is the best defense against threats.
- Staff Training and Awareness: The human element in cybersecurity should not be ignored. Proper training for cybersecurity staff and increasing awareness about potential threats are essential for a robust cybersecurity strategy.
Incorporating these best practices into the software development process enhances software application security. It safeguards the application against potential attacks and enhances the reputation as a reliable software provider, affirming a commitment to data security.
Consequences of Neglecting Cyber Security Measures
Having discussed cybersecurity in detail and its importance in software development, let us see what the consequences of neglecting cybersecurity measures are.
- Data Breaches: This is one of the most significant repercussions of neglecting cybersecurity. Organizations face a heightened risk of data breaches and fail to protect their systems and sensitive data. Cyberattacks may lead to unauthorized data access, theft, or exposure of confidential data. Breaches further result in financial losses, harm to reputation, and legal consequences.
- Financial Loss: Organizations and individuals may face severe financial losses as a result of cybersecurity incidents. A significant cost is involved in recovering from a cyber-attack, including investigating the attack, restoring systems and data, and addressing legal or regulatory requirements. In a few cases, organizations may also face lawsuits, financial penalties, and loss of business.
- Reputational Damage: A cyberattack may compromise customer data, eroding their trust in the organization. The public perception of the organization’s ability to protect the information diminishes and tarnishes the reputation. Rebuilding trust and repairing a damaged reputation requires significant time and effort. All these potentially result in loss of customers, revenue, and market share.
- Legal and Regulatory Consequences: Organizations neglecting cybersecurity practices can result in non-compliance with applicable standards and regulations. Numerous jurisdictions, such as GDPR and HIPAA, mandate organizations to implement suitable security measures to protect personal information. Non-compliance with these standards may result in legal consequences, including penalties and legal action.
- Operational Disruptions: When a cybersecurity incident occurs, the overall organization’s operations are disrupted. This can lead to system downtime, diminished productivity, and disruption of crucial business processes. These disruptions, in turn, have a cascading effect on the organization’s customers, orders, and business activity.
As far as possible, organizations should not neglect cybersecurity practices. Instead, they should implement these practices to their maximum benefit.
Cybersecurity Tools and Technologies
The following table contains various available cybersecurity tools and technologies.
| Tools | Examples |
|---|---|
| Code Scanning Tools | These code scanning tools automatically detect vulnerabilities in source code:
|
| Web Application Firewalls (WAFs) | WAFs filter and monitor HTTP traffic, protecting web apps from attacks like SQL injection and XSS. |
| Container and Cloud Security Tools | The following tools ensure secure container orchestration and cloud environments:
|
| Endpoint and Network Security | The following tools come in handy:
|
The Role of DevSecOps
DevSecOps stands for Development, Security, and Operations. It is an extension of DevOps and is responsible for security throughout the CI/CS pipeline. Read: The Role of QA in DevSecOps.
The following are the benefits of DevSecOps:
- It offers automated vulnerability scanning.
- DevSecOps helps detect threats early.
- It helps with faster remediation.
- Collaborates between dev, ops, and security and supports all three aspects.
Here are the tools used in DevSecOps:
- GitLab Security Scanner
- Snyk
- Dependabot
- Vault by HashiCorp for secrets management
Read: DevSecOps vs. DevOps: Differences, Tools, and Strategies.
Looking Ahead: Future Trends in Cybersecurity
Some of the emerging trends in cybersecurity are:
- AI in Cybersecurity: Artificial Intelligence (AI) has been increasingly used in cybersecurity for:
- Threat detection
- Behavior analytics
- Automated response systems
Conversely, attackers are also using AI to automate and obfuscate attacks. Read: Cybersecurity Testing in 2025: Impact of AI.
- Quantum Computing Threats: As quantum computing advances, some traditional encryption algorithms, like RSA, may become obsolete. Post-quantum cryptography is an emerging field that addresses this.
- Zero Trust Architecture: The Zero Trust model assumes no implicit trust and insists on verifying every access request. This zero-trust principle is gaining momentum, more as organizations embrace remote work and distributed environments.
Conclusion
Cybersecurity is a foundational aspect of responsible and reliable software development. As cyberattacks become more sophisticated and systems become more interconnected, secure development practices must be a shared responsibility across the development, security, and operations teams.
By encouraging a culture of security awareness and training, staying ahead of emerging threats, and embracing the secure development cycle, organizations can build software that performs and protects.
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












