What is SSO Testing?
|
|
We are in the era of Single Sign On (SSO). If you have a Google account or a Facebook account, you can easily get to work on other websites. These sites might ask you to choose a way to log in, and you can choose to use one of these primary credentials. Apart from not having to remember a million different usernames and passwords, the SSO approach helps eliminate repeated logins, gives faster access to other applications, and reduces those pesky “forgot password” issues.
If you’re testing any application, you might need to test the SSO login, too. Or maybe you’ve implemented SSO as a part of your application and want to test it. Whatever the case, here is all you need to know before you get started with SSO testing.
What is SSO?
Imagine you work in a big office building with many rooms (email, calendar, file storage, etc.). Single Sign-On (SSO) is like having one key that unlocks many doors. Without SSO, you’d need a separate key for each room – a different username and password for each app or service. But with SSO, you only need one key (one login), and it lets you into all the rooms you’re allowed to access. If you sign in once, you can move between apps without having to log in again each time.
Key Components of SSO
While the exact architecture can vary depending on the implementation and protocols used, here are the common core components involved in a typical SSO system:
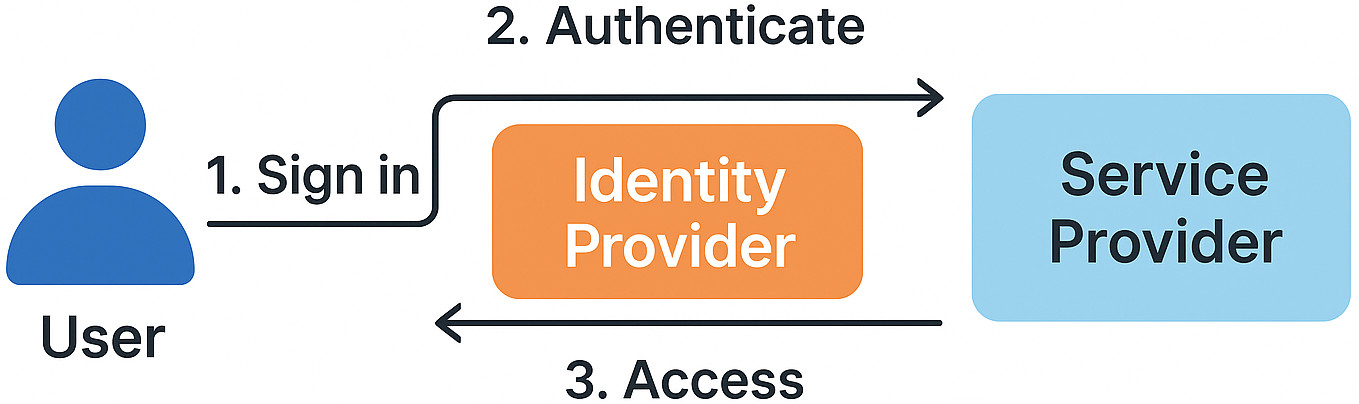
- User: This is the individual trying to access multiple applications.
- Service Provider (SP): These are the applications or services that the user wants to access (e.g., a CRM system, an email platform, a project management tool). The SP relies on the Identity Provider to verify the user’s identity.
- Identity Provider (IdP): This is the central authority that manages and authenticates user identities. It stores user credentials and verifies them when a user tries to log in. Once authenticated, the IdP issues a security token or assertion. Examples of IdPs include corporate directory services (like Active Directory), cloud-based identity management services, or social login providers (like Google or Facebook, in some contexts).
- Authentication Token (or Assertion): This is a digital credential issued by the IdP after successful authentication. It contains information about the user’s identity and is presented to the SP as proof that the user has been authenticated. The SP trusts the IdP and validates this token to grant user access.
- Trust Relationship: For SSO to work, a trust relationship must be established between the Service Providers and the Identity Provider. This involves configuring the SPs to recognize and trust the IdP’s authentication decisions and the security tokens it issues. This trust is often established through the exchange of metadata or certificates.
- SSO Agent (Optional): Sometimes, an agent or connector is deployed on the Service Provider’s side. This agent intercepts user access requests, communicates with the IdP to verify the user’s authentication status, and handles the exchange and validation of security tokens.
- User Agent (Typically the Web Browser): This acts as the intermediary, facilitating communication and redirection between the user, the Service Provider, and the Identity Provider.
How SSO Works
- User Attempts Access: A user tries to access a Service Provider (an application).
- Redirection to IdP: The SP determines if the user is authenticated. If not, it redirects the user’s browser to the Identity Provider.
- User Authentication at IdP: The user interacts with the IdP, providing their credentials (if they haven’t already logged in to the IdP in the current session). The IdP verifies these credentials.
- Token Issuance: Upon successful authentication, the IdP generates an authentication token or assertion containing information about the user’s identity.
- Redirection Back to SP with Token: The IdP redirects the user’s browser back to the Service Provider, including the authentication token.
- Token Validation: The SP receives the token and validates its authenticity by communicating with the IdP or by verifying its digital signature based on the established trust relationship.
- Access Granted: If the token is valid, the Service Provider establishes a session for the user and grants access to the application without requiring further login.
- Subsequent Access: If the user tries to access another Service Provider that participates in the same SSO system, their browser may already have a valid session or token from the IdP. The new SP can then verify the user’s identity with the IdP (often silently, without requiring the user to re-enter credentials) and grant access.
Why Should You Do SSO Testing?
By testing your SSO implementation, you can make sure that the following problems are avoided.
- You Can Log in Without Issues: If there’s a glitch, you could get locked out of important apps — that’s frustrating! SSO testing checks if logging in and logging out work smoothly.
- Only the Right Doors Open: You should only access the apps you’re allowed to use. SSO testing makes sure that no one sneaks into apps they shouldn’t have access to. It keeps the wrong people out and the right people in.
- Security Stays Strong: Imagine if someone stole your key. Could they get into everything? SSO testing makes sure that your login (key) is secure, tokens aren’t reused, and hackers can’t trick the system. It protects your data and keeps your company safe.
- It Works Across all Apps: You might use many apps (email, files, chat, etc.). SSO testing ensures that all these apps work together smoothly with your single login. No weird bugs or surprises when switching between apps.
- A Smooth User Experience: No one likes typing passwords all day long. SSO testing helps keep the “log in once, access everything” experience working perfectly – so employees stay productive and happy.
SSO Testing Test Cases
You need to think about SSO in three parts: full flow from login to logout, after login, and after logout. Your test cases will revolve around these states. Here’s how you can go about it.
Authentication Flow Testing
This is the core of SSO testing and focuses on verifying the entire login and authentication process.
- Successful Login: Ensure users can successfully log in to the Identity Provider (IdP) and subsequently gain access to all integrated Service Providers (SPs) without being prompted for credentials again.
- IdP-Initiated Login: Test the scenario where a user logs in directly to the IdP portal and can then access the SPs through a dashboard or links without further authentication.
- SP-Initiated Login: Verify that when a user tries to access an SP directly, they are correctly redirected to the IdP for authentication and then seamlessly redirected back to the SP with access granted.
- ‘Remember Me’ Functionality: If implemented, test the “remember me” option to ensure users can maintain their logged-in state across browser sessions as expected.
- Session Management: Verify how user sessions are created, maintained, and terminated across the IdP and SPs. Ensure consistent session timeouts and proper logout functionality.
Security Testing
Security is paramount in SSO. This area focuses on identifying potential vulnerabilities like
- Token Validation: Ensure that the authentication tokens (e.g., SAML assertions, OAuth tokens) issued by the IdP are correctly validated by the SPs to prevent unauthorized access.
- Token Integrity: Verify that tokens cannot be tampered with during transit or storage. Check for encryption and digital signatures.
- Confidentiality: Ensure sensitive information within the tokens is protected from unauthorized disclosure.
- Authorization: While SSO primarily handles authentication (verifying who the user is), make sure that the information passed in the token allows the SPs to correctly determine the user’s authorization levels (what they are allowed to do).
- Logout Functionality: Thoroughly test single logout (SLO) to make sure that when a user logs out from one application or the IdP, their sessions are properly terminated across all connected applications. Test various SLO scenarios (IdP-initiated, SP-initiated).
- Vulnerability Scanning: Conduct security scans on the SSO infrastructure to identify potential weaknesses.
- Man-in-the-Middle (MITM) Attacks: Assess the system’s resilience against MITM attacks by ensuring secure communication protocols (e.g., HTTPS) are enforced.
Integration Testing
SSO involves different systems working together. This area verifies the seamless interaction between them.
- Communication between IdP and SPs: Test proper communication and data exchange between the IdP and all integrated SPs using the chosen protocol (e.g., SAML, OAuth, OpenID Connect).
- Metadata Exchange: If applicable, verify the correct exchange and processing of metadata between the IdP and SPs, which contains configuration information and trust anchors.
- Attribute Mapping: Test that user attributes (e.g., name, email, roles) passed from the IdP to the SPs are correctly mapped and interpreted by each application. This is crucial for personalization and authorization within the SPs.
- Error Handling: Verify that the system handles errors gracefully, such as incorrect credentials, network issues, or invalid tokens, providing informative messages to the user.
User Experience (UX) Testing
While not strictly functional, a good SSO implementation should be user-friendly.
- Seamlessness: Test that the transitions between applications after the initial login are smooth and don’t require any manual intervention from the user.
- Intuitiveness: The login process itself should be clear and easy for users to understand.
- Error Messages: Error messages during login should be clear, concise, and helpful.
- Performance: Evaluate the login and redirection times to make sure they are within acceptable limits and don’t cause user frustration.
Performance and Load Testing
Assess how the SSO system performs under various load conditions:
- Login Load: Simulate a large number of concurrent login attempts to ensure the IdP and SPs can handle the load without performance degradation or failures.
- Session Management Load: Test the performance of session creation and management under heavy usage.
- Scalability: Evaluate the system’s ability to scale as the number of users and integrated applications grows.
Compliance and Standards Testing
Test the SSO implementation adheres to relevant security standards and protocols (e.g., SAML 2.0, OAuth 2.0, OpenID Connect).
Cross-Browser and Platform Compatibility
Test the SSO functionality across different web browsers (Chrome, Firefox, Safari, Edge) and operating systems (Windows, macOS, Linux) to provide a consistent experience for all users.
Best Practices for SSO Testing

SSO Testing Tools
You can test SSO logins through functional testing, API testing, and even end-to-end testing. While you can test this manually, you may want to make use of automated testing so that after every release, your login is working. You can use different tools, like SAML-tracer to track login data for SAML or Postman to test tokens. However, it is better to use a test automation tool that lets you test a lot more, along with SSO login.
testRigor is a generative AI-based test automation tool that can simplify your testing endeavors. This cloud-based testing tool lets you test a variety of scenarios, including SSO logins across different platforms like the web, mobile, and desktop.
enter stored value "test-gmail" into "Email or Phone" click "Next" enter stored value "test-gmail-pass" into "Password" click "Next" generate PIN with google authenticator from stored value "MyQrCode" and save as "code" enter stored value "code" into "Enter code"
Complete test case details over here – How to Automate 2FA Login with TOTP using testRigor?
That’s how easily you can handle scenarios that might seem complex with traditional test automation tools like Selenium. Another great thing to note here, besides the ease of using plain English to write test cases, is that you need not worry about XPaths or CSS selectors for UI elements. testRigor intelligently recognizes the elements on the screen using AI.
testRigor offers many built-in commands that reduce your work manifold. For example, for a login field, you can simply use the “login” command once you save your username and password as test data. If you wish to build your own set of commands for reuse, you can do that as well! Two good things about this – first, you can use plain English to do this, and second, you can use AI to build and maintain these reusable rules.
testRigor understands the importance of security and hence supports SSO login as well. You can log into your testRigor account by configuring your preferred identity provider.
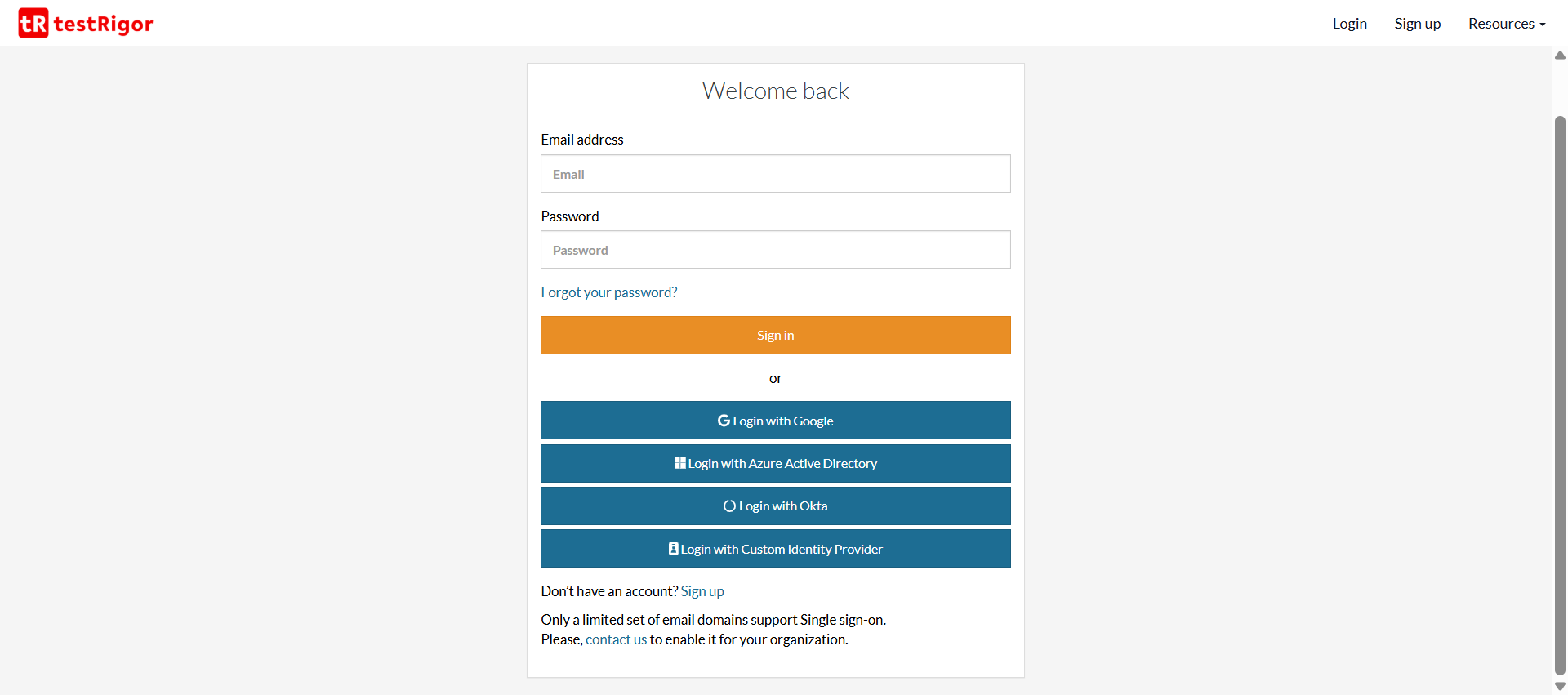
Read more about how testRigor supports SSO authentication with any identity provider.
You can do a lot more with testRigor. Here’s a full list of this tool’s capabilities and an All-Inclusive Guide to Test Case Creation in testRigor.
Final Note
Unless you’re building your own application, you may not need to test SSO login explicitly. However, it is a very important use case for most test scenarios these days as all applications invariably rely on SSO logins for security. With a smart test automation tool like testRigor, you can easily manage this scenario and focus on other complex ones that might require you to use your creativity.
Additional Resources
- Cybersecurity Testing: Impact of AI
- How to simulate login action using testRigor?
- Hybrid Testing: Combining Manual and Automated Testing
- Types of Defects in Software Testing
- The Best API Testing Tools
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












