What is Cryptography?
|
|
Digital communication is extensive, and information security has never been more critical. As data travels far and wide through digital mediums, from protecting defence and financial data, securing online transactions, safeguarding state secrets, and to enabling privacy on social media, cryptography has secured a central place in all secure communications. But what is cryptography, and how does it become so important? This article will answer these questions.
| Key Takeaways: |
|---|
|
We will cover the following in this article:
|
This article discusses all these points in detail and sheds light on cyber attacks and ways to mitigate them.
Cryptography: Definition and Principles
Cryptography is the science and practice of securing communication by using encryption (converting data into an unreadable format) and decryption (restoring encrypted data into a readable form) techniques to protect information from unauthorized access.
Cryptography comes from the Greek words Kryptos, meaning “hidden”, and graphein, meaning “to write”.
Basic Cryptography Process
A simple process of cryptography is shown below:
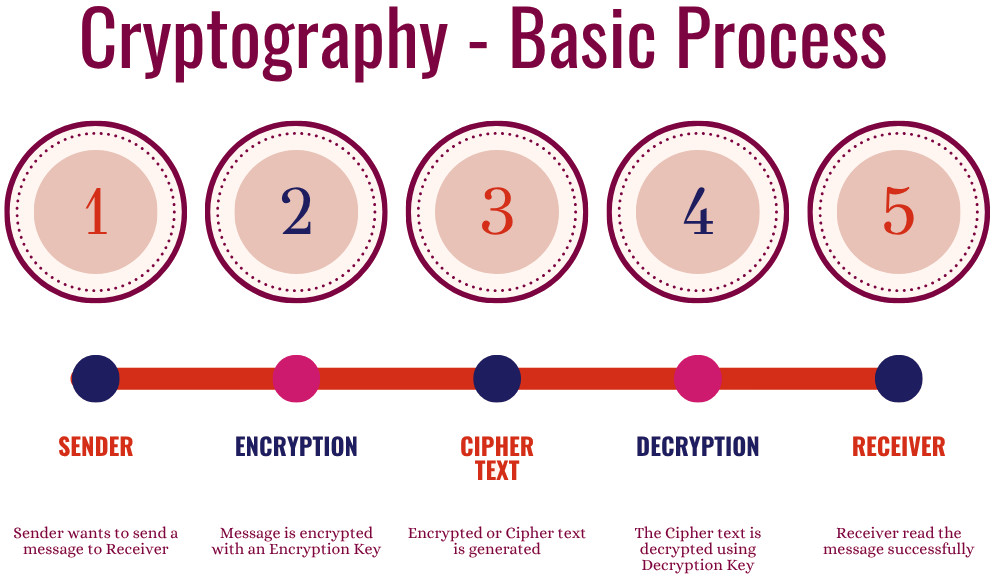
- The cryptography process “codes” the information so that only the person for whom a message was written can read and process it.
- The sender first encrypts the information using an appropriate encryption method.
- The encrypted text (ciphertext) is then passed on to the receiver.
- The ciphertext is decoded or decrypted at the receiver’s end using the decryption key.
- Since only the valid receiver possesses the decryption key, the information will be decoded by the legitimate receiver only.
An encryption/decryption key is a specific secret key that is used to encrypt/decrypt information. Cryptography is a cybersecurity practice that combines various disciplines, such as computer science, engineering, and mathematics, to create complex codes that hide a message’s true meaning. It is used to obscure any form of digital communication, including text, images, audio, or video.
Cryptography Core Principles
Though modern cryptography has grown significantly more advanced over time with the invention of new methods and algorithms, the general idea of the process remains the same. It is based on the following core principles:

- Confidentiality: Encrypting the information to be communicated prevents unauthorized access. This encrypted information can only be accessed by the person for whom it is intended.
- Integrity: Once information is encrypted, it cannot be altered in transit or in storage between the sender and the intended receiver without any changes being detected. In simple words, data integrity should be maintained.
- Authentication: The identities of the sender and receiver, as well as the origin and destination of the information, are confirmed.
- Non-repudiation: The sender of encrypted information cannot deny their intention to send the information.
A Brief History of Cryptography
The origin of cryptography can be traced back to ancient Egyptian hieroglyphics. However, it still remains vital to securing information and communication in transit and preventing it from unauthorized access. A brief timeline of cryptography is given below:
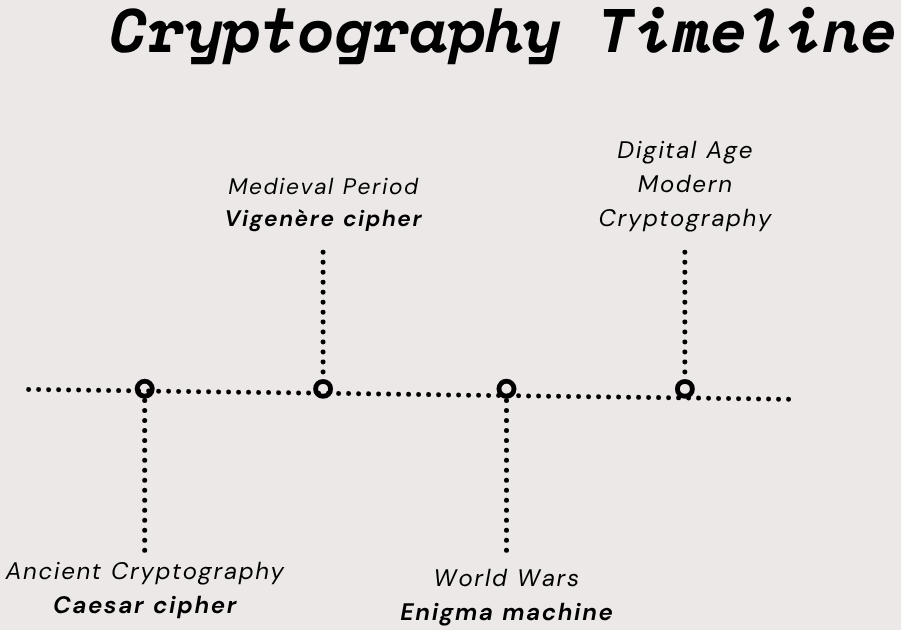
Ancient Cryptography
It has been thousands of years since cryptography was invented. One of the earliest examples of cryptography is the Caesar cipher, which Julius Caesar used to protect military messages. The Caesar cipher simply shifted or jumbled up the letters of the message by a fixed number of places. For example, with a shift of 4 letters, “HELLO” becomes “LIPPS”.
Medieval Period
During the medieval period, more complex ciphers were developed, like the Vigenere cipher, which used a keyword to shift letters differently throughout the message. These ciphers were stronger but still vulnerable to frequent analysis.
World Wars
Dramatic advancements in cryptography were witnessed during World Wars I and II. A classic example is the German Enigma machine, which encoded military information. The Allies’ efforts to break it, led by Alan Turing, were ultimately instrumental in shortening the war.
Digital Age
Computers and smartphones have become the main mediums of communication in the digital age, and with them came Modern Cryptography. Modern cryptography uses algorithms like DES, RSA, and AES and hash functions that provide scalable and robust encryption for digital communication.
Cryptographic Protocols and Techniques
Cryptography uses various protocols and architectures apart from algorithms. The following table lists these protocols and techniques:
| Protocoles/Techniques | Uses |
|---|---|
| SSL/TLS |
|
| VPN |
|
| Digital Signatures |
|
| Digital Certificates |
|
| Hash Function |
|
| Public Key Infrastructure (PKI) |
|
Cryptographic/Encryption Algorithms
Cryptographic systems use a set of procedures known as cryptographic or encryption algorithms to encrypt and decrypt data to secure communications among devices, machines, and applications. These algorithms are also known as Ciphers.
A cipher suite uses:
- One algorithm for encryption,
- Another algorithm for message authentication, and
- Another for key exchange.
This process is embedded in protocols and written in software on operating and networked computer systems. The process involves the following steps:
- Public and private key generation for data encryption/decryption.
- Digital signing and verification for message authentication.
- Key exchange for verifying the sender and receiver.
Types of Cryptography
There are different types of cryptography, based on the keys, algorithms, and access criteria. The following are the main types discussed here:
1. Symmetric Key Cryptography
This is also known as secret key cryptography. Symmetric key cryptography uses a single key for both encryption and decryption. In symmetric cryptography, the sender and receiver of an encrypted message will have access to the same shared secret key. Caesar’s cipher is an early example of a single-key or symmetric key system. This system worked by transposing each letter of the message forward by a specific number of letters (typically three) since Caesar’s generals knew the key, so they could unscramble the message by reversing the transposition.
Advantages:
- Speed: The encryption process is comparatively fast.
- Efficiency: Single-key encryption is well-suited for large amounts of data and requires fewer resources.
- Confidential: Effectively secures data and prevents others without the key from decrypting the information.
Disadvantages:
- Key distribution is challenging, as there is always a question: how do you securely share the key?
Common Algorithms used:
- Advanced Encryption Standard (AES)
- Data Encryption Standard (DES) (now obsolete)
- Blowfish
2. Asymmetric Key Cryptography
This is also called public key cryptography, which uses one private and one public key. The data is encrypted with a public and private key. For decryption, the recipient requires its private key as well as the public key.
Asymmetric cryptography enables secure key exchange over an insecure medium without sharing a secret decryption key. Public keys and private keys are different and are kept secret. In this way, asymmetric encryption adds a layer of security because an individual’s (sender or receiver) private key is never shared.
Advantages:
- Security: Asymmetric encryption enables secure communication and digital signatures.
- Robust: Public key cryptography offers more benefits, providing confidentiality, authenticity, and non-repudiation.
- Distribution: Solves the key distribution problem.
Disadvantages:
- Resource-intensive: Asymmetrical encryption is slow and requires greater resources, which can be prohibitively expensive in some cases.
Common Algorithms Used:
- Rivest-Shamir-Adleman (RSA)
- Elliptic Curve Cryptography (ECC)
- ElGamal
3. Hash Functions
Hash function cryptography does not require a key. It uses mathematical equations to generate a fixed-length hash message for any arbitrary message length. Hash functions are one-way or irreversible and are used to ensure data integrity. Hashing is the process of mapping a key to a specific value, called a hash or hash value. A hash function transforms a key or a digital signature, and the hash value and signature are sent to the receiver. The receiver uses the hash function to generate the hash value and compare it with the one they received in the message.
Applications:
Hashing is used in the following applications:
- Password storage
- Data integrity verification in databases
- Blockchain and digital signatures
Standard Hash Algorithms Used:
- Secure Hash Algorithm 256-bit (SHA-256)
- SHA-3
- MD5 (considered insecure now)
- MD6
Applications of Cryptography
Cryptography is needed almost everywhere. Some major applications include:
1. Internet Security
When users browse secure websites, cryptography protects them from man-in-the-middle (MitM) attacks and eavesdropping. The Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols use public key cryptography to protect data transmitted between the web server and client.
2. E-commerce and Online Banking
Cryptography can confirm or verify a user’s identity and authenticate their access, such as when logging in to an online banking account or accessing a secure network. Electronic signatures, or e-signatures, created with cryptography are used to sign important documents online and are frequently enforceable by law. These digital signatures can be validated to prevent fraud and forgery.
3. Cryptocurrencies and Blockchain
Cryptocurrencies like Bitcoin and Ethereum are built on complex data encryption, which requires significant computational power to decrypt. New crypto coins are “minted” and enter circulation through these decryption processes. Cryptocurrencies use advanced cryptography to safeguard crypto wallets, verify transactions, and prevent fraud. Read: Blockchain Testing: How to do it?
4. Secure Communication
Message authentication, whether for a simple private conversation or sharing classified information, uses end-to-end encryption to protect two-way communication, such as video conversations, instant messages, and email. End-to-end encryption provides a high level of security and privacy for users and is widely used in communication apps like WhatsApp and Signal.
5. Access Control
Cryptography is used to implement access control lists (ACLs) that define permissions for various users and groups, providing them with role-based access control. It can also verify user identities and grant access to systems, resources, and networks, ensuring that only authorized users can access sensitive information.
Cryptography in Everyday Life
Without realizing it, cryptography is also in day-to-day life:
- Logging into secure websites (HTTPS), including banking and e-commerce
Read: Test Automation for FinTech Applications
- Swiping credit and debit cards
- Sending a message via WhatsApp
- Unlocking your phone using facial recognition
- Access cloud storage, including GDrive and Google Photos
Challenges in Cryptography
Cryptography faces several challenges that are external and internal. Some of these key challenges are:
- Quantum Computing Threat: There is a growing concern that quantum computers can break many current cryptographic systems, especially those based on factoring large numbers (RSA) or discrete logarithms (ECC). This has necessitated the development of post-quantum cryptography or quantum-resistant cryptographic algorithms. Read: What is Quantum AI?
- Algorithm Vulnerabilities: Cryptographic algorithms can be vulnerable to cyberattacks if implemented incorrectly or have inherent weaknesses. As modern cryptography relies on mathematical complexity, advancements in computing power, notably quantum computers, could render it obsolete. Read: Cybersecurity Testing in 2025: Impact of AI.
- Implementation & Integration: Cryptographic algorithms should be implemented appropriately to ensure security. Integrating cryptography into complex systems like networks and applications can be challenging. Different cryptographic systems should be interoperable, and guaranteeing this poses a challenge. Poor coding practices, insecure key storage, and side-channel attacks compromise cryptography algorithms.
- Key Management: Safeguarding and distributing cryptographic keys is a logistical and technical challenge. Symmetric cryptography uses a shared secret key, and distributing it securely without exposing it to attackers is a significant concern. Asymmetric cryptography uses public and private key pairs, and system security depends on the difficulty of deriving the private key from the public key.
- Human Factors: Human errors can break the strongest cryptographic systems. Social engineering attacks, weak passwords, and improper key storage can lead to security breaches. Insider threats, such as individuals misusing access privileges, also pose a threat.
Future Trends in Cryptography
Here are the emerging trends in cryptography:
- Homomorphic Encryption: Ability to perform computation on encrypted data without decrypting it. This is useful for privacy-preserving data analysis and cloud computing. Read: Cloud Computing as a Career for Software Developers.
- Zero-Knowledge Proofs: Proving knowledge of a value without revealing it. Such a feature is ideal for identity verification and blockchain applications.
- Lightweight Cryptography: Algorithms in constrained environments like IoT devices use less power and memory, making lightweight cryptography ideal. Read: IoT Automation Testing Guide: Examples and Tools.
- Multi-Party Computation (MPC): MPC allows multiple parties to compute a function while keeping their inputs private.
Conclusion
Cryptography is the protective, invisible armor of the digital era. Cryptography has seen continual evolution and increasing sophistication from ancient Caesar ciphers to modern-day complex algorithms. As digital technologies advance, threats also become more advanced. Cryptography will remain vital in these situations, carving a future of secure communication, protected transactions, privacy, and trust.
Whether you are a developer, policymaker, consumer, or ordinary individual, understanding cryptography and its workings is essential for navigating the increasingly complex and interconnected digital world.
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












