What is Fuzz Testing?
|
|
Ever wondered what lurks in the darkest corners of your software, just waiting to crash your application or, worse, expose sensitive data? Traditional testing methods are great at making sure that your code does what it’s supposed to do, but they often miss the truly bizarre inputs and unexpected scenarios that can lead to catastrophic failures. This is where fuzz testing comes in. It acts like a digital wrecking ball, deliberately feeding your software a barrage of malformed, unexpected, or random data to uncover those hidden vulnerabilities that traditional tests simply can’t find.
Key Takeaways
|
What is Fuzz Testing?
Imagine you’re testing an app, and you start typing in random characters, gibberish, or numbers that the app isn’t designed to handle. Most of the time, the app should handle these strange inputs without any problem. But sometimes, it might crash or behave in ways that developers didn’t expect. That’s what fuzz testing is all about – catching those moments before they can be exploited by someone with bad intentions.
Thus, fuzz testing, or fuzzing, is a technique used to find bugs or security issues in software by feeding it random, unexpected, or even crazy inputs. The main goal of fuzz testing is to help developers find hidden bugs or vulnerabilities that might be overlooked during normal testing. It’s like trying to break something in order to make it stronger.
History of Fuzz Testing
The concept of fuzz testing was first introduced in 1988 by a researcher named Prof. Barton Miller at the University of Wisconsin. Prof. Miller was working on a project to study how programs handled unexpected inputs. While working on a project to test the robustness of Unix utilities, he intentionally fed them random input. Their initial results showed a surprisingly high rate of crashes and failures, which demonstrated the vulnerability of software to unexpected data. They published a paper on this work, and the term “fuzz” (referring to the random data) was coined then.
At first, fuzz testing was a fairly simple technique. It was mostly used to find crashes or program failures. Over time, though, as software grew more complex and security threats became more serious, fuzz testing evolved. Developers started to use fuzz testing not just to find bugs, but to discover security vulnerabilities that could be exploited by hackers.
In the early 2000s, fuzz testing gained even more attention. Tools were created to automate and improve the fuzz testing process. These tools made it easier for developers to run fuzz tests on large and complex systems and helped uncover vulnerabilities in popular software like operating systems, web browsers, and servers.
Types of Fuzz Testing
- Mutation-based Fuzzing: This is the most common type of fuzz testing. In mutation-based fuzzing, you start with a valid input (like a file or a request the software is supposed to handle) and then change it randomly. These changes might include things like flipping bits, changing numbers, or modifying the structure of the input. The idea is to create unexpected versions of a valid input and see how the software reacts.
- Generation-based Fuzzing: In generation-based fuzzing, instead of starting with a valid input, the tool creates completely new, random inputs from scratch. These inputs are designed based on certain rules or models that describe how the software expects its inputs to look. It’s like guessing what the input should look like and then trying out different combinations to see what causes problems.
- Coverage-guided Fuzzing: Coverage-guided fuzzing takes things a step further by focusing on areas of the program that haven’t been tested yet. The idea is to keep track of which parts of the code the fuzz test has already covered and then keep testing the parts that haven’t been explored. This helps improve the chances of finding new bugs and vulnerabilities.
- Dumb Fuzzing: This type is as simple as it sounds – the tool just throws random data at the software with little to no consideration of what the program expects. It’s fast but might not find as many issues.
- Smart Fuzzing: On the other hand, smart fuzzing tries to understand the software’s behavior and inputs better. It might use algorithms or models to generate more meaningful inputs that are more likely to uncover bugs. It’s a more advanced and targeted approach.
- Protocol Fuzzing: Protocol fuzzing focuses on testing network protocols (the rules that software follows to communicate over a network). The goal here is to send random or malformed messages over a network to see if the software handling the protocol can handle unexpected inputs.
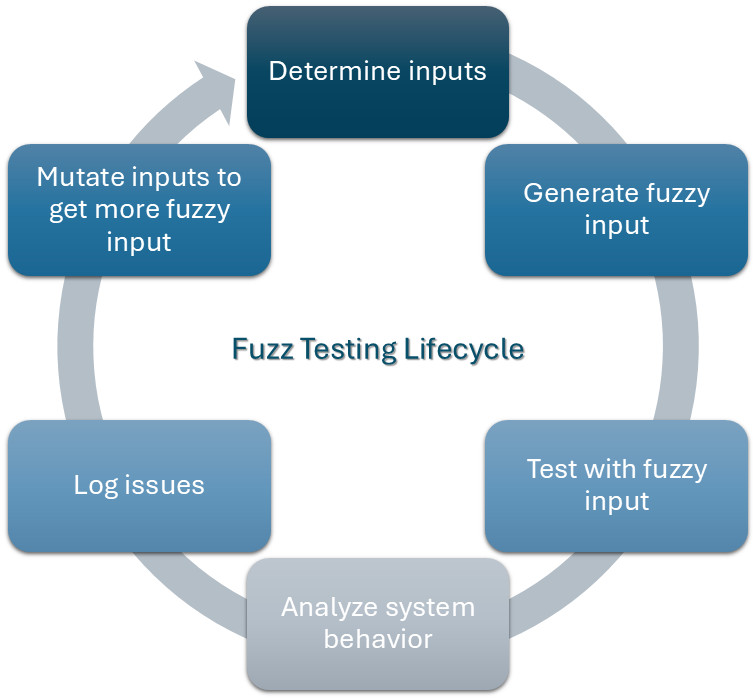
How does Fuzzing in Testing Work?
Irrespective of the type of fuzz testing you do, the general approach goes something like this.
- Choose the Software to Test: First, you need to choose the software or system you want to test. This could be anything from a web application to an operating system or even a small program that handles user inputs, like a calculator app.
- Generating Fuzzy Inputs: Once the software is chosen, the fuzz testing tool creates random inputs. These inputs can be anything: gibberish text, random numbers, or even malformed data that the program isn’t expecting. The idea is to simulate real-world mistakes or unexpected actions that users might make when using the software. For example, if the program expects a number, the fuzz tool might send a string of letters instead. If the program expects a date, it might send a completely random sequence of characters.
- Feed the Fuzzy Inputs to the Software: The next step is to send these inputs into the program or system. The software receives the inputs just as if they were from a real user. The difference is that these inputs are strange and unpredictable.
- Monitor the Behavior: After sending the inputs, the fuzz tester monitors how the software behaves. If everything works fine and the software doesn’t crash, the test continues with different inputs. But if the software crashes, freezes, or behaves unexpectedly, that’s a sign that there might be a bug or vulnerability.
- Reporting the Findings: When the fuzz tester finds an issue (like a crash, error, or vulnerability), they report the problem. Developers can then investigate the issue further, fix it, and make the software more robust and secure.
- Repeat with More Fuzzy Inputs: Fuzz testing is often an ongoing process. The tester doesn’t just run one set of random inputs. They keep generating and testing new inputs in hopes of finding more bugs, especially in different parts of the software that haven’t been tested yet.
Applications of Fuzz Testing
Let’s look at some of the most common applications of fuzz testing.
- Finding Security Vulnerabilities: One of the most important uses of fuzz testing is to find security vulnerabilities in software. Hackers often try to exploit weaknesses in programs to cause harm or steal data. Fuzz testing helps discover vulnerabilities like buffer overflows, memory leaks, and other weaknesses before attackers can take advantage of them.
- Testing Software Robustness: Fuzz testing is great for testing how robust a software program is. Robustness means the software can handle a wide range of situations without crashing. By sending random or invalid inputs, fuzz testing checks how the software handles unexpected scenarios.
- Network Protocol Testing: Many software systems communicate over networks, and these interactions need to be tested for reliability and security. Protocol fuzzing is a specific type of fuzz testing used to test network protocols, like HTTP or FTP, by sending unexpected data over the network to see how the software responds.
- Improving Web Application Security: Web applications are often targets for hackers because they handle sensitive user data. Fuzz testing can be used to test the security of web applications by trying to feed them unpredictable inputs, such as strange characters or corrupted data, to see if they can withstand attacks.
- Validating File Parsers: Software that reads or parses files (like a PDF reader, image viewer, or video player) can be vulnerable to attacks when it encounters malformed or unexpected files. Fuzz testing is used to test these file parsers by feeding them corrupted or random files to see how the software reacts.
- Automated Testing in Continuous Integration: Fuzz testing can be automated and integrated into the software development pipeline, known as Continuous Integration (CI). This means that every time new code is added to a software project, fuzz testing can automatically run to ensure that the new code doesn’t introduce new vulnerabilities or crashes.
- Embedded Systems and IoT Devices: Embedded systems and Internet of Things (IoT) devices are becoming increasingly common, and they often have very specific hardware or communication protocols. Fuzz testing can be used to test these devices for security vulnerabilities and stability issues, especially since many of these devices are connected to the internet and could be vulnerable to attacks.
Fuzz Testing Tools
- AFL (American Fuzzy Lop): AFL is one of the most well-known fuzz testing tools. It works by mutating existing data and sending it to the program for testing. It’s open-source, fast, and highly effective. AFL is particularly good at detecting memory corruption bugs and other vulnerabilities in system-level software.
- LibFuzzer: It is another popular fuzz testing tool that focuses on testing code at the function level. It works by providing random inputs to a function and checking for crashes or unexpected behavior.
- Peach Fuzzer: It is a comprehensive fuzz testing tool that focuses on testing network protocols, file formats, and other complex systems. It can generate random inputs based on predefined models and test how the software handles those inputs. Peach Fuzzer is often used for security testing in commercial applications.
- OSS-Fuzz: This is a cloud-based fuzz testing service that helps open-source software projects find vulnerabilities. It integrates with GitHub, automatically running fuzz tests whenever new code is committed. It’s free for open-source projects and continuously runs fuzz tests on many widely used software libraries, such as OpenSSL and libpng.
- FuzzTest: This is a commercial fuzz testing tool that offers both mutation and generation-based fuzzing. It’s designed to test various types of software, from web applications to embedded systems.
Conclusion
Today, fuzz testing is an important part of modern software development and cybersecurity. It has grown from a simple idea into a powerful tool for improving the reliability and security of software in all kinds of industries. You’ll mostly see it being used by developers and security professionals to find weaknesses before malicious attackers can exploit them.
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












