Defect-based Testing: A Complete Overview
|
|
Software quality is paramount in ensuring that the software application performs as expected. With emphasis on software quality, software testing has evolved from being an afterthought (Kind of: If time permits, we will test it) to becoming a strategic priority (testing first). Out of many test approaches used today, defect-based testing stands out as a highly targeted and intelligent testing approach.
| Key Takeaways: |
|---|
|
This article examines the defect-based testing approach, its significance, and how organizations can effectively implement it within a modern testing ecosystem.
What is a Defect in Software Testing?
A defect in software testing is defined as “any deviation between the real outcome of the software and its expected results”.
A defect, also known as a bug, refers to any error or flaw in a software application that results in unexpected, inaccurate, or unintended outcomes. A defect may occur at any stage of the software development lifecycle (SDLC).
Examples of Defects
Some of the examples of defects are:
- When a user enters a specific set of data, an application crashes. This is a defect, as the application is unable to process the data.
- A log-in function is not working when valid credentials are passed to it.
- A webpage loads only in Google Chrome but does not load properly in other browsers.
Generally, everything that does not work as expected in a software application is a defect. However, there are various types of defects.
Read: Masked Defects Uncovered: Shining Light on the Hidden Flaws
Types of Defects
If you are aware of the kind of defect in the product, it can help with proper reporting and processing. Here are the types of defects one encounters during software testing:
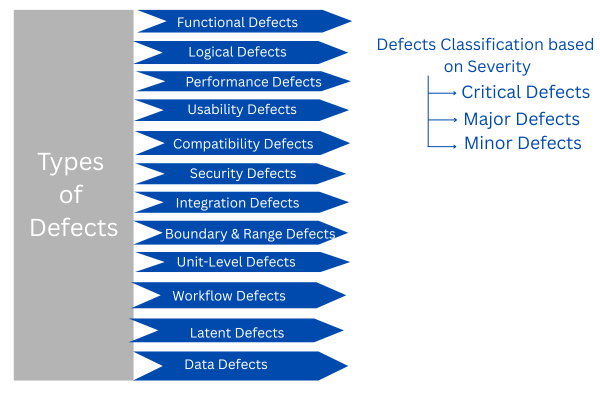
Based on how severely the defect impacts the application, it is classified as:
-
Critical Defects: These defects pose a safety hazard or cause complete failure of the product. Critical defects are the most serious and should be taken care of immediately to ensure business continuity.Examples include an application crash or a database connection failure that prevents the application from carrying out its functions.
- Major Defects: These types of defects significantly impact the product’s function or usability but are not a safety risk. At most, they may lead to customer complaints or product rejection.
- Minor Defects: These are cosmetic issues and do not affect the product’s performance or safety. Issues encountered in UI, such as spelling mistakes and non-alignment of components, are minor defects that have an effect on the aesthetics of the UI.
Read:
- Mastering Defect Management: Understanding Severity vs. Priority in the Life Cycle
- The Strategy to Handle Defects in the Agile Development Methodology
- Defect Triage in Software Testing
The types of defects are as follows:
Functional Defects
These are the defects that affect the functionality of the application. These are the most common defects and occur when an application does not function as expected. For example, when a payment gateway is unable to process transactions even with correct data in an e-commerce application, it affects the functionality of the application and is a functional defect.
Logical Defects
Errors in the application’s logic are logical defects. Usually, these are the outcomes of faulty algorithms or incorrect code conditions. A calculator program that executes arithmetic conditions incorrectly because of a misplaced operator can be highlighted as a simple example.
Performance Defects
When software’s performance is not up to the mark in areas such as response time, resource usage, and load handling, performance defects emerge. An application would be reported for performance problems if it crashed under the stress of a large number of users or took an excessive amount of time to process data.
Usability Defects
These are the defects related to application usability and have a negative effect on the user experience as a whole. These defects do not impact the software’s functionality, but they could make it annoying or challenging to operate. A few examples of usability defects are unreliable UI elements, confusing navigation, or a lack of accessibility features.
Compatibility Defects
When a software application does not work seamlessly on different devices, browsers, and platforms, compatibility defects arise. A webpage that loads perfectly in the Google Chrome browser but does not completely load in other browsers is a compatibility defect.
Security Defects
Security defects threaten the user’s privacy and data integrity and can lead to exploitable vulnerabilities, data leaks, or illegal access to the system. These defects are mostly severe and must be detected and resolved immediately to maintain compliance and trust.
Integration Defects
When multiple software modules or systems don’t work properly when integrated, it is called an integration defect. These issues frequently appear during integration testing. Integration defects may include data format mismatches or API responses.
Boundary and Range Defects
These are edge defects that arise when the system fails to handle values at the edge of input ranges appropriately. For example, input of 0 or 101 should be reported if a form accepts age values ranging from 1 to 100. Failure to handle such inputs is a boundary defect.
Unit-Level Defects
Unit-level defects are limited to a specific application module or component and are detected during unit testing. These defects are often detected early in the development cycle and are usually caused by coding errors.
Workflow Defects
Workflow defects occur when there is a problem in the order or reasoning behind the application’s operations. For example, a user can check out without adding items to their cart, which is a broken workflow.
Latent Defects
Latent defects are invisible problems that occur in specific scenarios, such as a production environment, and do not typically occur in everyday situations. Such defects need in-depth analysis and monitoring, and are specifically difficult to detect during testing.
Data Defects
If an application uses or generates Incorrect or inconsistent data, it results in erroneous outcomes referred to as a data defect. Incorrect data handling in the database, losses during transfer, or subpar data mapping can all contribute to this issue.
Read: Types of Defects in Software Testing
Common Origins of Defects
A defect can originate from a wide variety of sources, some of which are mentioned here:
- Incomplete Requirements: Poorly defined, incomplete, or ambiguous requirements that create confusion and misinterpretation.
- Design Errors: A problematic software architecture or design can lead to defects.
- Coding Mistakes: Developers making mistakes in application implementation, such as syntax errors, logical, or algorithmic errors, can result in defects.
- Unidentified Defects: When testing is performed inadequately, defects can go unnoticed and seep into production.
- Defects Due to Software Environments: Differences in the software environments may also give rise to defects, primarily due to incompatibility.
The Defect Lifecycle in Software Testing
The defect lifecycle, also known as a bug lifecycle, refers to the lifetime of a defect, encompassing the journey it takes from defect identification to defect closure.
This defect lifecycle is a key component of defect management in software testing, which improves software quality, reduces costs, and enhances customer satisfaction.
The various stages in a defect lifecycle are:
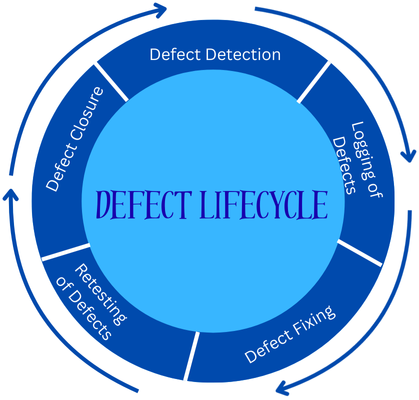
- Defect Detection: This is the first stage, where testers become aware of defects during testing activities when the software doesn’t behave as expected.
- Logging of Defects: Once defects are identified, they are logged into a defect tracking tool, accompanied by a detailed description that includes steps to reproduce, severity, screenshots, and a comparison of actual and expected results. Practically, defects are reviewed with a priority setting based on their magnitude and effect on the system during triage. This classification determines the defect priority, or the order in which defects should be corrected first.
- Defect Fixing: Based on the priority of defects, developers address the issues. A defect is analyzed, the root cause is identified, and the corresponding fix is applied.
- Retesting of Defects: In this stage, the fixed defect is verified to ensure that the defect has been rectified and no new defects have been introduced as a result of the fix.
- Defect Closure: Once the retesting of the defect is done, the defect is closed. If the fix was not as expected, it is reopened and dispatched to the development team for fixing.
What is Defect-Based Testing?
At this point, you are familiar with what a defect is and its associated details. The software testing approach based on defects is called defect-based testing.
Defect-based testing is defined as a software testing approach that relies on historical defects, known bug patterns, and common error-prone areas to design and prioritize test cases.

Where traditional testing is geared toward a wide-area coverage, defect-based testing is useful for an activity that gears towards targeted coverage – this means testers spend their time hanging out in the area where defects are most likely to show up. This means that the system under test is not fully in focus, but instead certain defect types that regularly occur in a system or business domain are.
Practically, defect-based testing is a process where tests are derived from known problems, historical defect types (or error taxonomies), and failure patterns. It does not substitute for functional or exploratory testing; rather, it supplements those by allowing more intelligent, focused, risk-driven testing. It is suitable for any level of testing, but works best during Systems Testing. Test cases can be formulated using the root cause analysis.
Why Defect-Based Testing Matters
Defect-based testing is crucial because it is a systematic, data-driven approach that minimizes business risks, improves software reliability and quality, and significantly reduces the cost of software development. This method focuses specifically on identifying and addressing actual flaws (defects or bugs) to prevent severe consequences in production environments.
The following are the reasons why defect-based testing is essential:
-
Real-World Systems Rarely Fail Randomly: In most applications, defects tend to cluster around specific modules, functionalities, or integration points. According to the Pareto principle, 20% of modules may contain 80% of defects.Using defect-based testing, testers can concentrate their efforts on this non-random defect distribution and identify the maximum number of defects.
- Costs of Defects Increase Over Time: The cost of bug fixing increases substantially the later it is found in the SDLC. Detecting defects in the early stages saves more time and resources than addressing them in deployment or production stages.
- Improved Test Efficiency: With defect-based testing, the team can prioritize meaningful tests over redundant ones, identify high-risk scenarios, improve test coverage based on actual system behavior, and reduce unnecessary manual efforts. Especially, AI-driven automation tools like testRigor help generate regression tests to prevent the reappearance of high-frequency defects.
- Minimizing Business Risk and Impact: Defects that leak into production result in serious adverse outcomes, including financial losses, data breaches, damage to brand reputation, and even system crashes or power grid malfunctions. Defect-based testing targets areas where failures are most likely to occur and would have the most significant impact, allowing teams to mitigate these risks proactively.
- Ensuring High Software Quality and Reliability: The primary goal of a software application is to provide the expected software functions and meet user requirements. By identifying and resolving defects, software application stability, performance, and security are improved, resulting in a better user experience and increased customer satisfaction.
- Optimizing Testing Efforts: By utilizing defect taxonomies (categorized lists of past defects) and risk analysis, testers can focus their efforts on high-risk, error-prone modules or components, rather than performing blanket testing across all modules or components. This targeted approach makes testing more efficient and effective.
Read:
Key Principles of Defect-Based Testing
Defect-based testing follows several foundational principles:
- Testing Shows the Presence of Defects: Testing detects defects, but it cannot prove that no defects remain in the software. The goal is to reduce the number of undiscovered defects.
- Exhaustive Testing is Not Possible: Testing every possible scenario, path, or input is not possible. Instead, focus should be on risk-based and prioritized testing.
- Early Testing is Crucial: Begin testing activities as early as possible in the SDLC to identify and correct defects at a lower cost.
- Defect Clustering: A small number of modules typically contain the majority of defects, as observed by the Pareto Principle. Hence, prioritize testing efforts on these defect-prone areas. Read: Defect Clustering in Software Testing
- The Pesticide Paradox: The same set of tests performed repeatedly eventually stops finding defects. Therefore, test cases must be regularly reviewed and updated to identify new issues and ensure their continued effectiveness. Read: The Pesticide Paradox: Sustaining the Effectiveness of Testing Methods
- Testing is Context-dependent: Appropriate testing approach, tools, and techniques chosen depend on the type of application (e.g., banking, e-commerce, gaming).
- The Absence of Errors Fallacy: A system is useless if it does not meet user requirements, even if it is 99% defect-free. Finding no defects does not mean the system is usable or valuable.
Types of Defect-Based Testing Techniques
Defect-based testing encompasses several specialized techniques as discussed here:
Error Guessing
This technique relies on the tester’s intuition, skill, and experience. Testers ‘guess’ or anticipate defects depending on past bugs discovered, known tricky scenarios, areas vulnerable to user input, and edge cases missed by developers.
Some examples include guessing errors, such as division by zero, null pointer exceptions, incorrect boundary validations, and invalid input combinations.
Error guessing technique is subjective, but it is highly effective when performed by experienced testers familiar with the application domain.
Read: What is Error Guessing Technique?
Fault-Based Testing
Fault-based testing technique involves deliberately designing tests to uncover specific types of faults, such as logic errors, data handling bugs, off-by-one errors, concurrency issues, and API contract violations.
This technique is often employed in safety-critical systems to deliberately introduce faults and observe system response. This is frequently used to test the robustness of fault-tolerant systems, embedded software, and industrial applications.
Defect Taxonomies
A defect taxonomy is a structured classification of common defect types. It is a list that may include input validation defects, data type mismatches, error handling deficiencies, memory management issues, or UI/UX consistency issues.
Using defect taxonomies helps teams ensure they test for entire categories of predictable defects.
Orthogonal Defect Classification (ODC)
ODC is an IBM-developed method that categorizes defects, enabling statistical analysis. Using this method, teams can pinpoint the location of defects, determine the causes of their occurrence, and identify which testing techniques are most effective.
ODC converts qualitative defect data into quantitative metrics, making it a powerful tool for large organizations.
Pattern-Based Testing
This testing technique examines commonly occurring patterns of defects within a system. For example, most errors occur during data synchronization, or login failures arise from incorrect session handling.
Once such patterns are identified, targeted test cases are created to verify and prevent their recurrence.
Defect-Based Testing Implementation
Implementing defect-based testing requires a structured approach as summarized below:
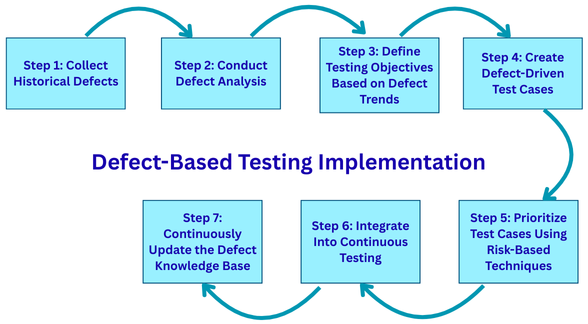
Step 1: Collect Historical Defects
Data is the foundation of defect-based testing. Information is collected from various sources, including bug tracking systems (such as Jira and Azure DevOps), production issue logs, CI/CD pipeline failures, and customer support tickets.
Defects are grouped by type, severity, module, frequency of occurrence, and impact on the application.
Step 2: Conduct Defect Analysis
Once defect data is collected, the next stage is to conduct defect analysis, which includes identifying high-risk areas, recognizing repetitive defect patterns, mapping defect causes, and understanding defect density per module.
Tools such as dashboards, charts, and heat maps are used in this phase to visualize where problems concentrate.
Step 3: Define Testing Objectives Based on Defect Trends
Based on the defect analysis results, objectives are defined, including validating input sanitization in all user-facing forms, enhancing API boundary testing, increasing tests for legacy modules, and expanding test coverage for high-frequency customer workflows.
Step 4: Create Defect-Driven Test Cases
In this step, test cases are designed to specifically validate previously failing scenarios, edge conditions known to trigger bugs, integration points that have historically been unstable, and areas where coding complexity is high.
Tests are also automated in this step, ensuring that defects do not recur in future releases.
Step 5: Prioritize Test Cases Using Risk-Based Techniques
Risk is determined by the probability of failure, the severity of potential defect impact, the complexity of code changes, dependency chains, and the frequency of usage.
Defect-based testing aligns naturally with risk-based testing strategies.
Step 6: Integrate Into Continuous Testing
In this step, defect-based tests are integrated into continuous testing, ensuring they are executed with every CI/CD cycle, following significant code refactoring, during regression testing, and before production releases.
Step 7: Continuously Update the Defect Knowledge Base
Once defect-based tests are integrated into the CI/CD cycle, the next step is to monitor defect trends as they evolve with the system transformation. Regular updates ensure the test suite stays aligned with new defects, changing architecture, evolving user behavior, and updated business logic.
Benefits and Challenges of Defect-Based Testing
The following table summarizes the benefits and challenges of defect-based testing:
| Benefits of Defect-based Testing | Challenges of Defect-based Testing |
|---|---|
| Higher Defect Detection Rate: This technique targets areas prone to failure, increasing the likelihood of finding defects early. | Requires High-Quality Defect Data: if bugs are not adequately documented, the effectiveness of defect analysis is compromised. |
| Cost Efficiency: Testing resources are utilized where they matter most, thereby reducing wasted effort. | Heavy Dependence on Tester Experience: Techniques like error guessing depend heavily on the tester’s deep domain knowledge. |
| Enhanced Test Coverage: Test coverage becomes more comprehensive, focusing on business-critical scenarios. | Not Sufficient as a Standalone Strategy: Defect-based technique must supplement, not replace, other methods such as functional, exploratory, and performance testing. |
| Reduced Regression Defects: Historical defect-driven regression tests prevent the recurrence of issues. | Requires Continuous Updates: Defect patterns evolve with the introduction of new features. Without continuous updates, defect-based tests become outdated. |
| More Innovative Use of Tester Expertise: Testers’ insights are captured and converted into reusable tests. | Risk of Overlooking Unknown Unknowns: Focusing solely on past defects may overlook new defect types introduced by emerging technologies or architectures. |
| Improved Product Stability: Focused testing reduces production incidents and increases system reliability. |
Real-World Example of Defect-Based Testing
Considers a retail ecommerce platform that frequently encounters defects in:
- Checkout flow.
- Payment system integration.
- Product search.
- Inventory sync with third-party APIs.
A defect-based testing approach can be designed as follows:
1. Checkout Flow
Tests for checkout flow validate edge cases like:
- Missing or incomplete shipping address.
- Invalid coupon codes.
- Failed payment authorization.
2. Payment Integration
Tests are designed for this module to ensure:
- Payment gateway timeouts are correctly handled.
- Proper error messages are used for declined cards.
- Tax and currency are accurately handled.
3. Product Search
In the product search module, tests may check:
- Incorrect indexing.
- Search latency under load.
- Auto-complete logic failures.
4. Inventory Synchronization
Tests related to inventory synchronization help to prevent issues such as:
- Mismatched stock levels.
- Delayed updates from external vendor systems.
- Out of stock product checkout.
The Future of Defect-Based Testing
As software systems become more complex and distributed, defect-based testing will evolve in tandem. Here are the key trends that stand out:
- AI-Driven Defect Prediction: Machine learning models can analyze code repositories, historical defects, commit histories, and developer behavior to predict where defects are likely to occur.
- Autonomous Testing: Automated testing tools, such as testRigor, enable the creation of natural language tests, self-healing test scripts, automatic test maintenance, and end-to-end regression coverage, dramatically reducing the burden of manual defect-based test creation. With further enhancements in technology, we will be able to have purely autonomous systems that can manage automated testing themselves.
- Continuous Quality Intelligence: Test generation pipelines will have inputs from real-time metrics from production (user journeys, errors, performance trends).
Conclusion
Defect-based testing is a robust, targeted, and data-driven approach that uses historical defect information and known failure patterns to optimize test case design. Instead of treating all functionalities equally, it intelligently focuses on areas most prone to failure, making testing more efficient, strategic, and aligned with business risk.
With defect-based testing, organizations strengthen their regression suites, prevent repeated failures, improve reliability, reduce testing cost and effort, and deliver a higher-quality product.
Defect-based testing combined with modern automation tools like testRigor becomes not just a methodology, but a competitive advantage.
| Achieve More Than 90% Test Automation | |
| Step by Step Walkthroughs and Help | |
| 14 Day Free Trial, Cancel Anytime |












